
DNS tunneling is a technique used by malicious actors to covertly transfer sensitive or unauthorized data from within an organization’s network to an external destination through the domain name system (DNS).
The DNS is primarily designed to translate IP addresses to domain names (i.e. www.todyl.com) that humans can read and understand, making it a fundamental component of internet communication. That said, the DNS protocol can also be exploited to send and receive data, making it a potential avenue for data exfiltration.
MITRE ATT&CK technique T1071.004 explains exfiltration, tunneling, and command and control (C2) over DNS and lists over 45 tools, malware families, and attacker groups that use it.
DNS tunneling is such a popular technique because it’s tricky to detect. DNS is a trusted protocol, so firewalls usually allow this traffic through. The amount of data hidden in each request is small, making it look like normal DNS activity.
Here’s the breakdown of how this process works:
There are many different tools attackers will use for DNS exfiltration and tunneling. Some of the most common include:
DNSSteal: DNS exfiltration tool for stealthily sending files over DNS requests
Iodine: Iodine is a free (ISC licensed) tunnel application to forward IPv4 traffic through DNS servers (IP over DNS)
DNScat: Enables 2 hosts to communicate entirely via the DNS protocol
Since DNS tunneling is difficult to protect, it’s crucial that you have a strong, layered security program in place.
First, ensure that your systems are protected with Endpoint Security (EDR+NGAV). Todyl’s Managed eXtended Detection and Response (MXDR) and Detection Engineering teams have built custom detections into our Endpoint Security module to ensure our partners are protected. A few of the detections we’ve built include:
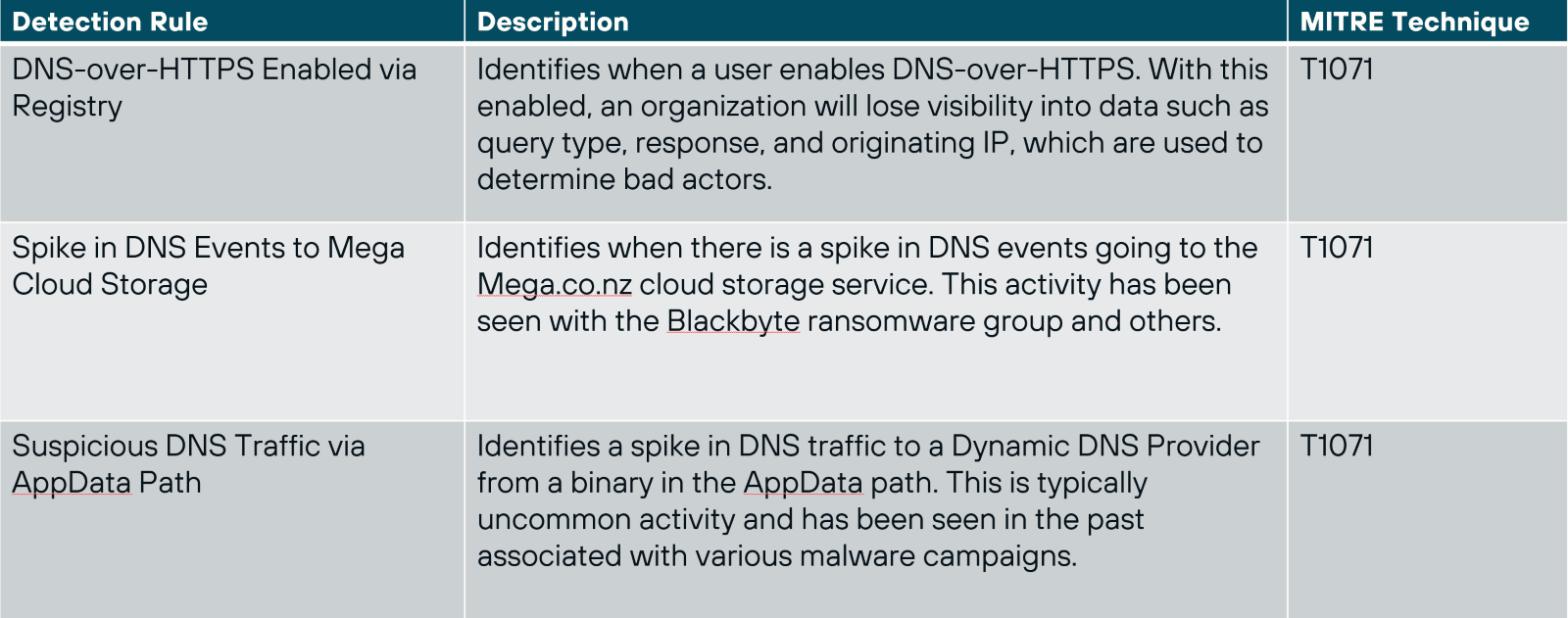
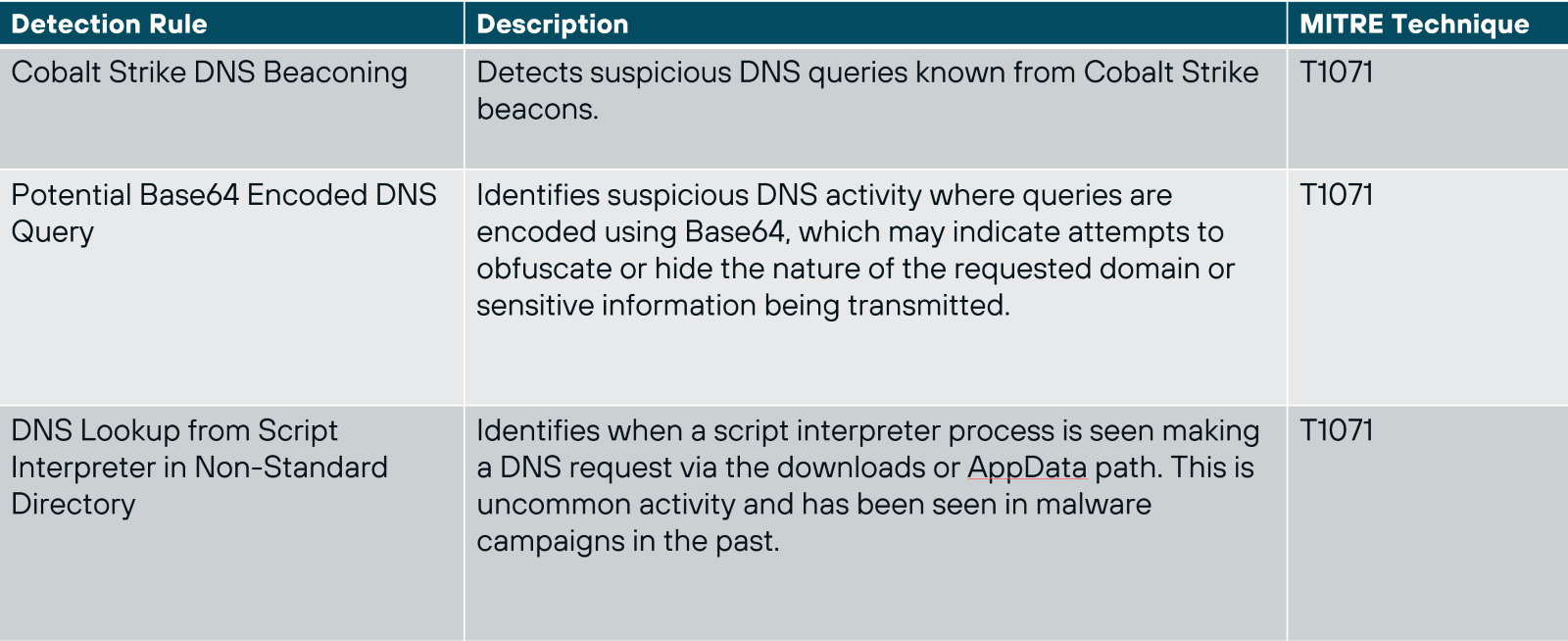
Todyl's Secure Access Service Edge (SASE) solution is also crucial to helping restrict unauthorized connections. Todyl’s SASE logs all DNS requests and has the option for SSL inspection to ensure your business is protected. Our Secure DNS feature allows you to further control how users can access domains based on policies like geolocation.
Not a Todyl partner? Click here to book a demo and learn more about our SASE and Endpoint Security modules, as well as the rest of the Todyl Security Platform.
Subscribe to receive the latest insights, news, and updates from Todyl.
