Improved visibility & investigation: Case Management in SIEM


In cybersecurity, you can only detect threats you can see, which is why it’s essential to have complete visibility into your environments. Visibility not only powers correlation and threat detection, but also empowers people to run threat hunts, conduct thorough investigations, and report the effectiveness of security programs.
Keeping this in mind, we decided to completely overhaul our Security Information & Event Management (SIEM) and Case Management System to provide unparalleled visibility, enhanced customizability, and a better user experience to drill into the data to understand in detail what’s occurring across your environment.
With this update, our goal was to streamline security operations, making it easier to investigate potential security incidents, report on cybersecurity posture with greater visibility, and easily search and threat hunt. Put together, these enhancements will help to free up time so our users can focus on other critical projects.
We achieved this by adding the following to the Todyl platform:
- Out-of-the-box persona-based dashboards and reports
- Highly customizable dashboards and reports with a visual widget library
- Powerful and responsive search leveraging keywords instead of query languages
- Case management system with new bucketing logic
Before digging into each of these features in detail, we wanted to help paint the picture of how the overhauled SIEM and Case Management System help improve visibility and streamline investigations.
Let’s take a living off the land attack as an example. The threat actor successfully executes a phishing attack to gain initial access to a business, eventually launching a PowerShell script to gain persistence and move laterally. It then calls back to the Command and Control infrastructure to pull down a malicious payload, such as a ransomware attack.
With the new SIEM and Case Management System, a case is created when an alert fires, grouping together similar alerts into a single event. Using our case bucketing logic, you gain a full picture of what happened, when it occurred, and where the threat exists. Each case provides the necessary detail that empowering teams to investigate with context as they understand exactly what’s going on. This can be viewed in either raw .json files or in a tabular format for ease.
This data gives additional context that you can use in the SIEM to run additional investigations and threat hunts, using our simplified search capabilities to drill down even further. In this case, you can take some of the data from the case, such as the hostname, to run additional searches against it to understand the broader context of the case to further accelerate the investigation of the case.
With that additional context set, let’s dig further into the features and capabilities.
Out-of-the-box persona-based dashboards and reports
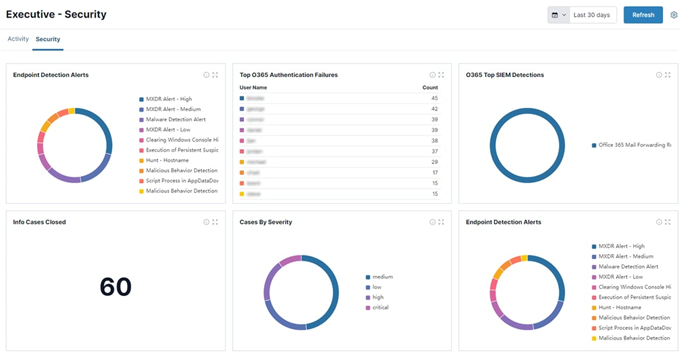
This update allows you to instantly drill into reports based on specific user profiles, or personas. As you can see in the example above, personas allow you to automate dashboards for high-impact roles like your executive and C-Suite employees to see information directly pertinent to those roles. For example, the “Executive – Security” serves up the most pertinent information to those with responsibility for cybersecurity, as well as those that need to manage the risk such as CISOs, CEOs, and Boards. This provides a quickly scannable view of issues that affect your organization from a security and operational perspective, allowing you to make informed decisions to better the business in those areas. Or, alternatively, you can gain insights relevant to a troubleshooting role like device status and Secure Global Network (SGN) traffic to facilitate problem solving.
With these new dashboards, you get a high-level overview of any detection alerts, authentication failures, cases involved, and more, to further your understanding. With a quick glance at a dashboard, you get a clear picture, enabling you and your team to act as quickly as possible. What's more, these are available for you out-of-the-box, so you don't have to do any legwork in the back end to build out the reports.
To further streamline investigations, the reports are also clickable. This allows you to drill down into the information you’re most concerned about, making it easy for teams to uncover potentially malicious activity.
Widget library for easy customization and creation
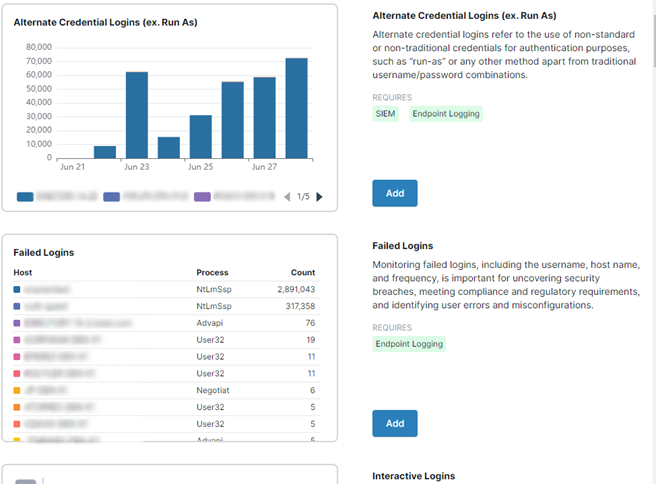
When it comes to dashboards and reports, we understand that one size does not fit all. To make it easy to customize and create visualizations, we’ve added over 100 new widgets to make your SIEM data as easy to consume as possible. Access the widget library to create reports depending on your needs and streamline your ability to get a full understanding of the ecosystem as well as drill into more specific areas as necessary.
Furthermore, many of these widgets are completely customizable and interactive so you can fine-tune them to best suit your needs. Also, you can tailor the widgets to highlight specific datasets to make reporting even easier and more digestible for your team.
Powerful search
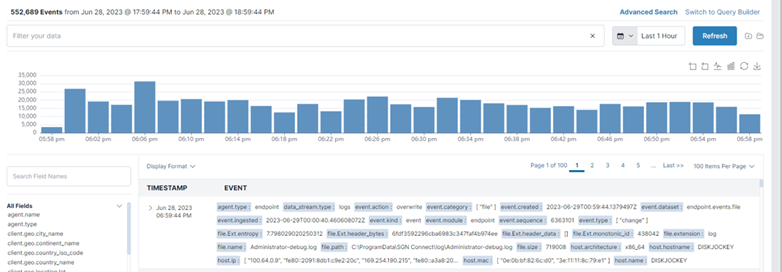
You don't need to be a query language expert to dive deep into your SIEM data. Our simplified search experience uses keywords to help you easily search across your data retention period in real-time. Now, you can create repeatable, saved search queries in just a few clicks that allow you to interact with data visualizations and share them easily across your team.
Completely rebuilt case management system
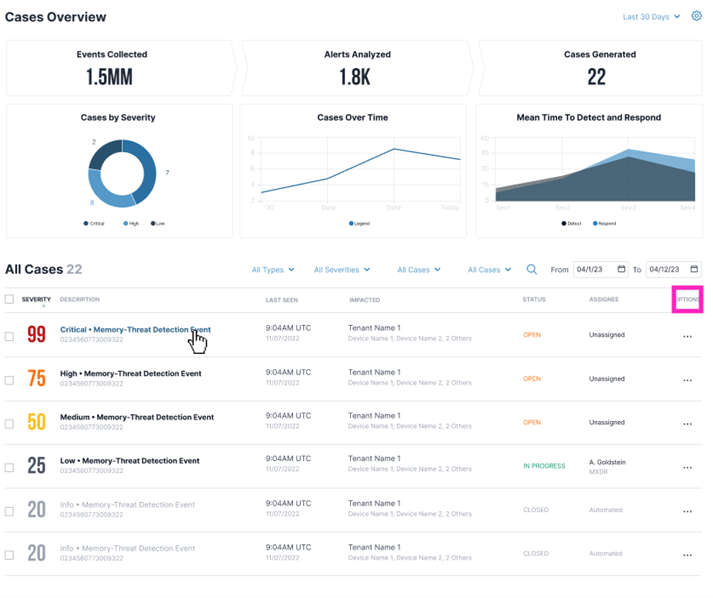
Todyl’s Case Management Module is a central repository for collecting, analyzing, and responding to specific alerts and incidents detected by the Todyl Security Platform. It enables rapid detection of security incidents and investigative workflows. Our revamped Cases functionality groups together multiple alerts and triggers into one overarching event so you can see the full extent of the activities within your environment. It also organizes them by severity according to the National Cyber Incident Scoring System as laid out by Cybersecurity and Infrastructure Security Agency. That way, your Security Operations Center knows when an issue in a specific tenant needs immediate attention and can address it accordingly.
Drilling deeper into a specific case, you can see everything associated with it: what the case pertains to, why it was assigned its severity, where in the environment it is affecting, and when it occurred. Cases v2 also maps the event to the MITRE ATT&CK framework so you can identify which tactics are at play and make educated estimates of what might be happening next.
A springboard for the future
These updates will help to greatly streamline investigations and improve visibility for all our users today. Looking to the future, the new SIEM and case management system will help us springboard multiple innovations we’ll cover on the blog in future updates. If you’d like to learn more about our overhauled SIEM or Case Management System, contact us today.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



