LAPSUS$, Okta, and Detecting Malicious Activity in Your Environments


LAPSUS$ breaches and attacks are front and center in the security news cycle. Large, multi-national organizations such as Okta and Microsoft are just the tip of the iceberg. In this blog, we provide background on LAPSUS$, a high-level overview of the Okta breach, and ways the Todyl Security Platform can help detect and identify if potentially impacted similar threats.
Background on LAPSUS$
LAPSUS$ is known for using social engineering to gain access to systems. They typically use a pure extortion and destruction model without deploying ransomware payloads. Unlike most threat actor groups that stay under the radar, LAPSUS$ does not try hard to cover its tracks. They go so far to announce their attacks on social media and often advertise their intent to buy credentials from employees of target organizations.
Their primary tactics include:
- Phone-based social engineering
- SIM-swapping to facilitate account takeover
- Accessing personal email accounts of employees at target organizations
LAPUS$ uses several methods focused on compromising user identities to gain initial access. These tactics range from deploying the malicious Redline password stealer to paying employees at targeted organizations (or suppliers/business partners) for access to credentials and MFA approval. As such, it’s imperative to implement strong MFA policies and ongoing security awareness training to defend against social engineering.
Overview of the Okta breach
In a statement from Okta's Chief Security Officer David Bradbury, they confirmed that Skyes Enterprises, a third-party Okta contracts with for customer services, was breached. Following investigations, Okta determined that RDP sessions were the root cause of the breach and the LAPSUS$ group had a 5-day window of access (January 16 to 21, 2022).
Okta confirmed that they limit their access levels with least privilege, restricting LAPSUS$'s ability to download customer databases, create or delete users, restricted access to product services, and denied access to source code repositories. According to Okta, 366 customers may be affected by this. However, Okta advised that their customers do not need to take corrective actions.
Detecting and identifying similar malicious attacks
After learning about the Okta breach, Todyl’s Head of Detection Engineering, Brent Murphy, added new detection rules across Todyl’s SIEM and Endpoint Security modules. These rules, specific to Okta, range from Brute Force or Password Spraying Attacks to Attempts to Reset MFA Factors for an Okta User Account. The rules include machine learning, static, threshold, and behavioral rules to provide broad detection coverage.
To test the effectiveness of the new rules, he leveraged Elastic Security’s Dorothy tool in a test environment. Dorothy helps security teams test their monitoring and detection capabilities for Okta environments by helping to simulate actions an attacker might take. It helps defenders test their security visibility and controls.
The screenshot below is from the Dorothy tool and highlights how an attacker could harvest users and admins from an organization, helping them prioritize social engineering targets.
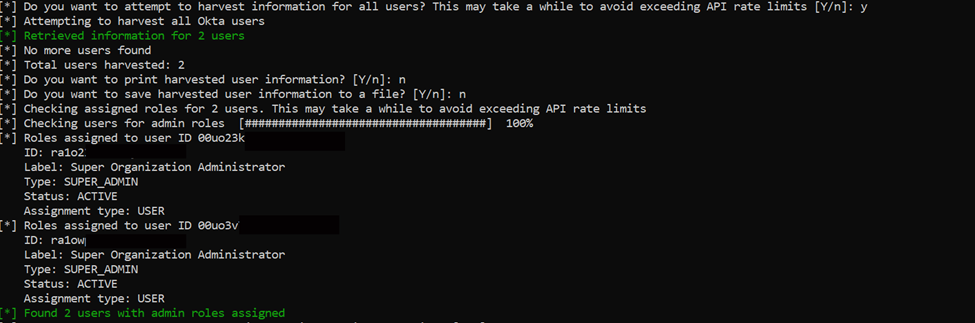
In the test environment, we found 2 users with admin roles assigned. Armed with this knowledge, it’s then possible to find and remove MFA, allowing the attacker to circumvent a critical security control.
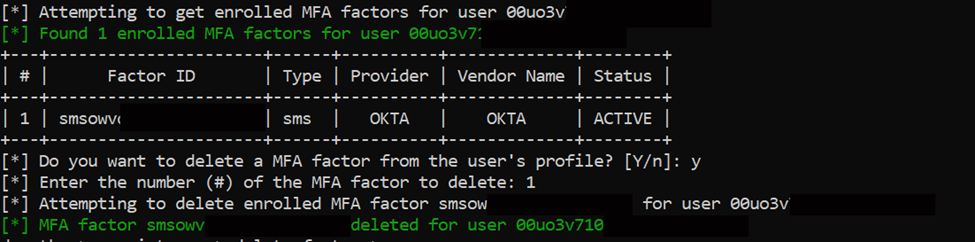
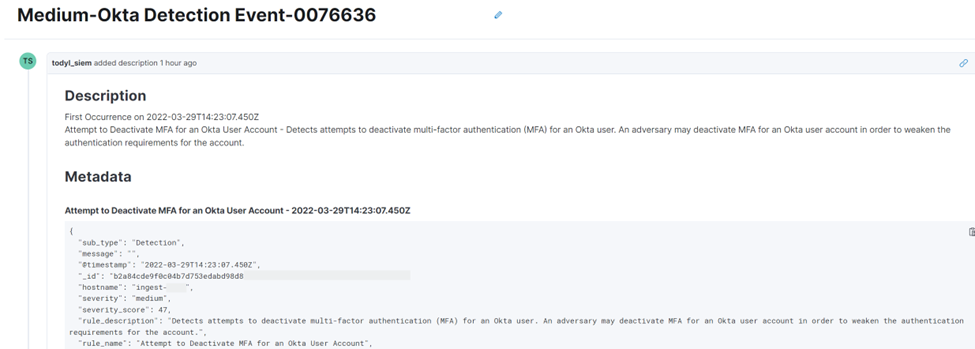
The new detection rules created a case, alerting that there was an attempt to deactivate MFA for an Okta user account. Cases group alerts and events into a single incident, providing teams with a workspace and single view to investigate alerts. Cases also include investigation tools, such as Timelines, to help unravel the root cause.
Todyl's SIEM can ingest logs from Okta, and includes pre-built dashboards in addition to the managed detection rules covered above. The pre-built dashboards cover events and incidents related to Okta failure events (e.g., log-on failures), actions taken in the environment (e.g., granting access, API calls, log geo-locations), and more.
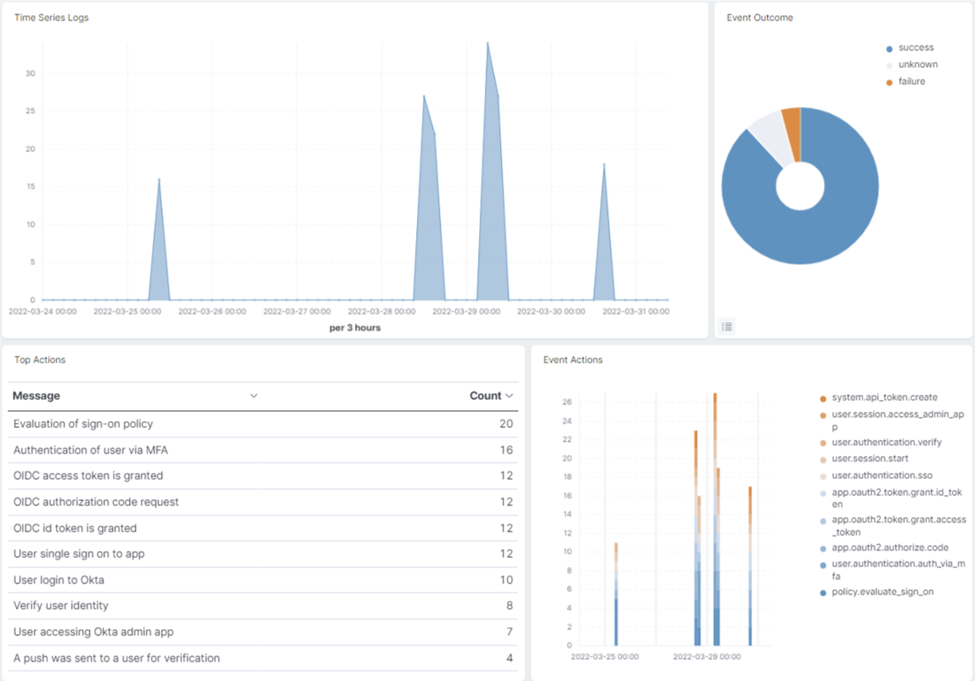
Beyond the dashboards, the Discover section helps to search through the logs. With it, you can get highly targeted and search within a particular "module" (e.g., Okta logs only), and then filter the results to parse out what you're looking for. This makes it easier to identify potentially malicious activity in Okta or any other environments.
If you’d like to learn more about how the Todyl Security Platform can help identify and detect similar malicious activity, contact us today.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



