How to Conduct Cyber Threat Hunts


Threat hunting is a crucial element of a strong security program. Automated security tools are not 100 percent effective against threat actor’s tactics, techniques, and procedures (TTPs) that continuously evolve, so human threat hunters add a critical layer of protection to earlier identification and detection of threats.
Threat hunting takes many different forms and is an often-used marketing buzzword, making it difficult to understand exactly what the process looks like and how it can take shape in the real world. In this blog, we’ll walk through the basics of common threat hunting methodologies and how to conduct a threat hunt, using an example of a recent threat hunt Todyl’s Managed eXtended Detection and Response (MXDR) team conducted.
Common threat hunting methodologies
Threat hunters operate on the assumption that an attacker already breached the network, initiating investigations to track down unusual behavior that may indicate the presence of malicious activity. These investigations typically fall into three categories:
1. Intel-Based Hunting
An intel-based approach to cyber threat hunting incorporates global threat intelligence that catalogs known Indicators of Compromise (IOCs) and Indicators of Attack (IOAs) associated with new threats. These indicators then become triggers that threat hunters use to find potential attacks or malicious activity that is already ongoing.
2. Hypothesis-Driven Hunting
Hypothesis-driven threat hunts are typically triggered by a newly identified threat through crowdsourced attack data. This hunting methodology aligns to the MITRE ATT&CK framework, using global threat intelligence to identify APT (advanced persistent threat) groups and malware attack tactics, techniques, and procedures (TTPs). Once new TTPs have been identified and published, threat hunters analyze data from their own environments, looking for any signs that these new behaviors could point to a lurking threat.
3. Custom Threat Hunting
A third approach to threat hunting is custom hunting that combines powerful data analysis and machine learning to sift through a massive amount of information and detect irregularities that may suggest malicious activity. These irregularities become new leads that security analysts use to identify potential threats.
All three of these approaches are human-powered efforts that leverage threat intelligence resources with advanced security technology to proactively protect an organization’s systems and data. The most effective cyber threat hunting strategies incorporate all three approaches to ensure all hidden threats are contained as quickly as possible.
How to conduct threat hunts
Threat hunts vary in length and complexity, but typically steps fall into one of three stages:
1. Trigger or hypothesis
A trigger or a hypothesis is an event or a piece of data that points threat hunters in the direction of a specific system or area of a network that requires their attention and further investigation. A trigger can be many things, such as newly identified TTPs that trigger proactive threat hunting.
2. Investigation
In the investigation phase, a threat hunter uses detection technologies such as EDR (Endpoint Detection and Response) to dive deep into reported data from the potentially compromised system or network. The investigation stage continues until the activity is deemed to be normal or a full picture of all malicious activity has been created.
3. Resolution
The final stage is resolution, which involves threat hunters communicating relevant malicious activity to operations and security analyst teams so they can respond to the incident and contain the threat. The data gathered can be fed to automated detection, and in some cases prevention, solutions to improve their effectiveness without human intervention going forward.
Throughout the entire process, threat hunters constantly gather information on an attacker’s actions, TTPs, and goals. They use this data to patch vulnerabilities and prevent malicious activity in the future.
Threat hunting in action
When performing threat hunts, Todyl’s MXDR team often employs hypothesis-driven cyber threat hunting, an effective method discussed previously. This threat hunting methodology involves taking known indicators or signs of an incident and searching across a greater dataset for signs of this behavior to identify other hosts impacted by the threat.
For example, during an incident investigating a new malware outbreak of the “IcedID” malware family, Todyl’s detection engineers identified a new method where attackers tricked users into downloading a file that contains malicious code. When a user unknowingly opens this file, it infects the host with the IcedID malware.
Typically, IcedID malware campaigns trick a user into viewing a website, and then downloading an executable file. Figure 1 below details what the process view looks like in these cases.
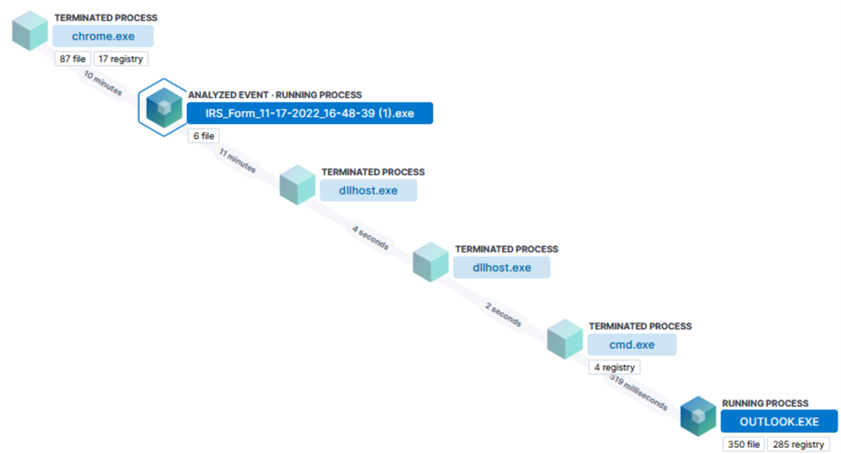
In Figure 1 we see Chrome downloading “IRS_Form_11-17-2022-16-48-39(1).exe,” and after execution, the malware launches cmd.exe and outlook.exe. The malware then uses Outlook to send out additional malware samples to the infected host’s contacts.
With the newer variant of IcedID, we see email attachments containing a .zip file, which then loads a malicious .iso file. These new TTPs help avoid common detections for this malware strain.
Todyl’s Endpoint Security (EDR + NGAV) and SIEM modules log the chain of activities for investigation by the MXDR team, who then goes in and investigates each issue.
After identifying the new TTPs for this malware strain, the MXDR team took these indicators and searched across our wide data set to see if we could identify other hosts that experienced these same indicators.
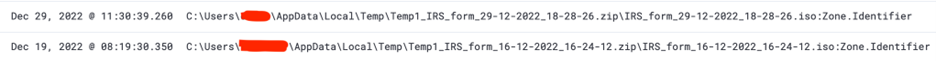
In Figure 2 we see two separate organizations impacted by the same type of malware strain. The IcedID campaigns are slightly different, as noted by the difference in file names.
Once our team’s hypothesis is proven, they create a rule to identify all events relating to this behavior in the future by leveraging the “Custom Rule” feature within the Todyl Security Platform, shown in Figure 3 below. Now that a custom rule is created, our MXDR team is immediately alerted every time this behavior appears so they can quickly investigate and remediate.

Learn from top security specialists with Todyl’s MXDR
Threat hunting is crucial in a security program, but conducting threat hunts is extremely time consuming and requires deep security expertise. Todyl’s MXDR team acts an as extension of your team, bringing additional resources and expertise than most businesses can’t support in house.
The Todyl team consists of NSA analysts, Naval cybersecurity specialists, and leaders at enterprise incident response companies who leverage global threat insights, intelligence sources, and sophisticated technology to conduct proactive threat hunting.
To learn more about how Todyl can help your business deliver stronger security, schedule a demo with our team today.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



