Threat Advisory: PwnKit Local Privilege Escalation


On January 25, 2022, a Local Privilege Escalation Vulnerability was publicly disclosed by Qualys in a Linux binary named “Polkit”, formally known as PolicyKit.
In this post, Brent Murphy, Head of Detection Engineering, and Aaron Goldstein, Head of Security Operations and Incident Response, explain more about what Polkit is, how the exploit works, ways to mitigate the threat, and how to use Todyl's Managed Cloud Security Information & Event Management (SIEM) Threat Hunting Dashboard to identify any vulnerable systems.
Quick facts on PwnKit
- Impacted OS/Application: All Polkit versions from May 2009 onwards are vulnerable on every major Linux distribution.
- Potential Impact: Severe, the CVSS Impact Score is 7.8 out of 10
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction Required: None
- Active Exploitation: There are multiple Proof-of-Concept (PoC) exploits available currently. At the time of publishing, it's unknown if there are any active exploitations.
- Countermeasure Recommendations: Many distributions of Linux are working to address the vulnerability with software patches, however, immediate remediation is possible by moving the SUID bit from vulnerable pkexec binaries:
chmod 0755 /usr/bin/pkexec.
What is Polkit?
Polkit is a utility that enables non-privileged processes to interact and communicate with privileged ones. The associated binary pkexec can be used similarly to the command sudo, meaning that it can elevate the privileges of a command.
PwnKit exploitation
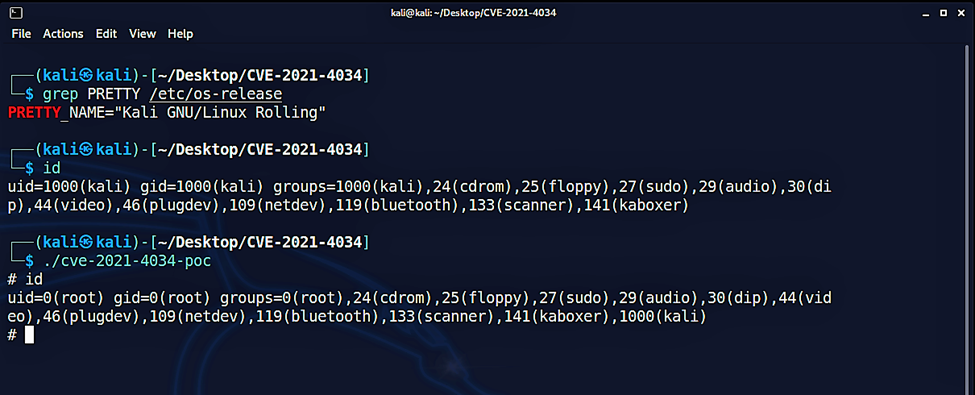
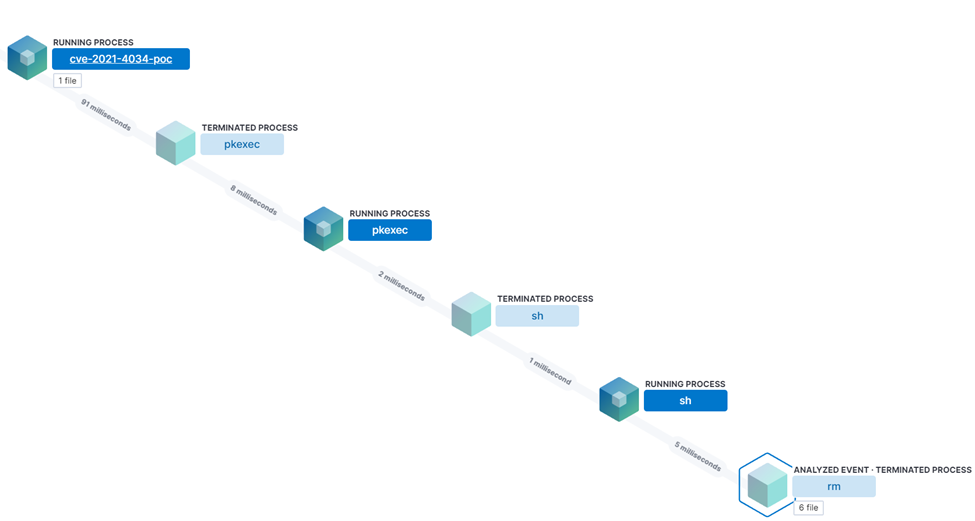
The PwnKit exploit involves an out-of-bound write command to pass an argument that overwrites an environment variable, which would typically be unalterable by an unprivileged user. Running a PwnKit exploit allows an attacker to go from a standard user account to root-level access with ease.
At the time of writing this blog, several PoC exploits are publicly available for download. While this exploit doesn’t allow for remote execution, it can be chained with other exploits to provide threat actors with unfettered access to a compromised system.
Remediation
Many distributions of Linux are working to address the vulnerability with software patches. Immediate remediation is possible by removing the SUID bit from vulnerable pkexec binaries. For most Linux variants, the command to perform this task is:
Todyl detection and response
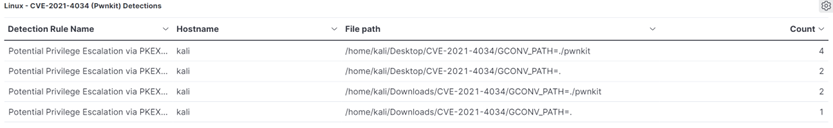
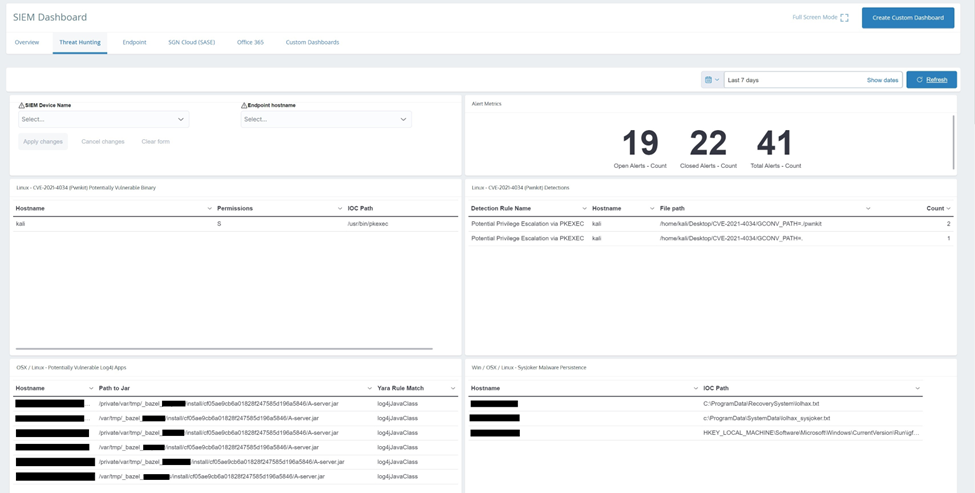
We are closely monitoring developments for this vulnerability and active exploitation in the wild. New detection rules are live to identify attempted exploitations via the Endpoint Security product, and the Threat Hunting Dashboard in SIEMv2 helps to identify potentially vulnerable instances of the binary pkexec by looking at the file permissions. Both SIEMv2 and Endpoint Security are new products available to our current partners by request.

See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



