SIEM: How Does it Work and What are the Benefits?


Cybercrime is one of the largest threats to modern business operations. According to Cybersecurity Ventures, the annual cost of cybercrime is predicted to hit upwards of $8 trillion USD this year.
Businesses need comprehensive visibility across their environments for real-time, correlated threat detection to identify active threats to their security. Doing so, however, is difficult given the state of modern work environments.
Remote workers, cloud adoption, and increased reliance on SaaS have led to a decentralization of IT resources, resulting in a much larger attack surface area. Typically, businesses implement multiple cybersecurity-focused point solutions to protect their users, data, and resources. Unfortunately, most of these tools lack integration, further obscuring visibility and limiting the ability to accurately detect threats.
As a result, threat actors have many places to hide in plain sight. With so many different endpoints, infrastructure options, technologies, and services at play, businesses of all types can find it difficult to keep track of everything. In the case of IT service providers, this complexity is multiplied and magnified as their number of clients increases.
Armed with a Security Information and Event Management (SIEM) solution, businesses can gain full visibility across the entirety of their environments to power comprehensive, effective threat detection.
What is SIEM?
SIEM provides comprehensive visibility across security and technology stacks. In practice, it enables organizations to:
- Monitor activity across their various resources
- Correlate activities across multiple different systems
- Detect threats to business operations
- Investigate the root causes of those anomalies
- Respond accordingly to either prevent a breach or stop an ongoing one
A SIEM performs real-time analysis to detect unusual activity and generates alerts to prompt teams to take appropriate action. With it, businesses can make informed decisions to strengthen their security posture; monitor, alert, and respond to attacks; and detect a wide range of threats. SIEM aggregates data in one centralized pane of administrative glass for IT and security teams to investigate and remediate issues faster.
The best SIEM solutions go a step further, correlating detected events into a single, manageable case of related activity per event. Leveraging event correlation and cases allows security teams to better understand the root cause and extent of a breach, powering faster investigations and more informed remediation steps. Teams can also drill into past events to see what went wrong and adjust their practices as necessary to prevent similar activities from happening in the future.
How does it work?
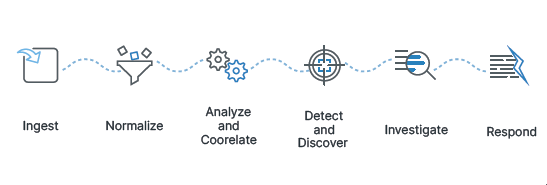
In practice, a SIEM solution collects data from across the IT environment, aggregates it based on type, and analyzes for behaviors, both standard and out of the ordinary. To do so, SIEM integrates with:
- SaaS apps
- Cloud-delivered infrastructure
- Endpoints
- On-prem servers and resources
- Networks
… and everything in between. That way, IT and security practitioners have a comprehensive view of their entire organization.
The best SIEM solutions go a step further, leveraging machine learning (ML) to power advanced analytics engines that examine data flow in real-time. Combining this with preset rules that define anomalous behavior allows teams to detect threats quickly. The SIEM alerts IT and security teams of these potential threats, allowing for further investigation and remediation.
Businesses can also build reports in their SIEM to gain a better understanding of their environment at large. Doing so helps build a better security posture moving forward. For example, by integrating with a productivity app like Office 365, you can create ML rules to detect scenarios like impossible travel. For example, if a user logs in from Denver, and then logs in from Romania a half-hour later, ML flags that as an impossible situation and alerts admins. Rules like these help businesses identify potential email compromise when a user logs in to one location, and then logs in somewhere far away within a defined period.
Benefits of SIEM
Given the prevalence of cyberattacks in the modern era, the use of SIEM provides many benefits to an organization.
- Quicker detection and response times: In a security event, the ability to respond efficiently and effectively is critical as an alert can escalate into a full breach in a matter of minutes. SIEM provides insights across all connected endpoints and resources, ensuring that nothing is missed, and threats can be addressed swiftly.
- Identification of a wide range of threats: Threat actors are constantly evolving their tactics, techniques, and procedures. Over time, a business’s attack surfaces change as well. SIEM keeps businesses informed through real-time visibility and continuous threat detection thanks to routine updates based on third-party intelligence, as well as ML-informed behavioral analysis.
- Insights into employee behavior: With remote work, IT practitioners have less direct visibility over employees’ day-to-day activities. SIEM provides a view across all IT resources into what happens day in and day out—both regarding productivity and potential insider threat actors.
- Forensic investigation and reporting: In the case of a security event, IT and security operations teams need to understand what happened and why. SIEM’s historical data pieces together the various assets and resources involved, allowing for a clearer understanding of an event and a better sense of how to combat similar attempts in the future.
- Proof of regulatory compliance: Many organizations of all sizes face government and industry-imposed regulatory compliance requirements. Through SIEM, businesses can source reports in a matter of minutes to streamline audits and prove compliance more effectively.
- Return on investment: Although not apparent initially, the other benefits of SIEM culminate in major savings for an organization, both in overhead and the potential costs associated with a security breach. For example, by leveraging SIEM reports, CIO/CISOs as well as IT service providers can demonstrate effective security controls to identify and prove business value.
Learn more
SIEM is a critical solution for businesses to stay informed about what’s occurring within their IT environments and detect threats across their organization. If you want to learn more about how to find the best SIEM for your business, read our blog, What to Look for in a SIEM Provider for a full list of considerations and questions to ask when evaluating your options.
For a full rundown of what SIEM can provide your business, check out our eBook.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



