Threat Advisory: spyboy and The Vulnerable Driver TTP


Summary
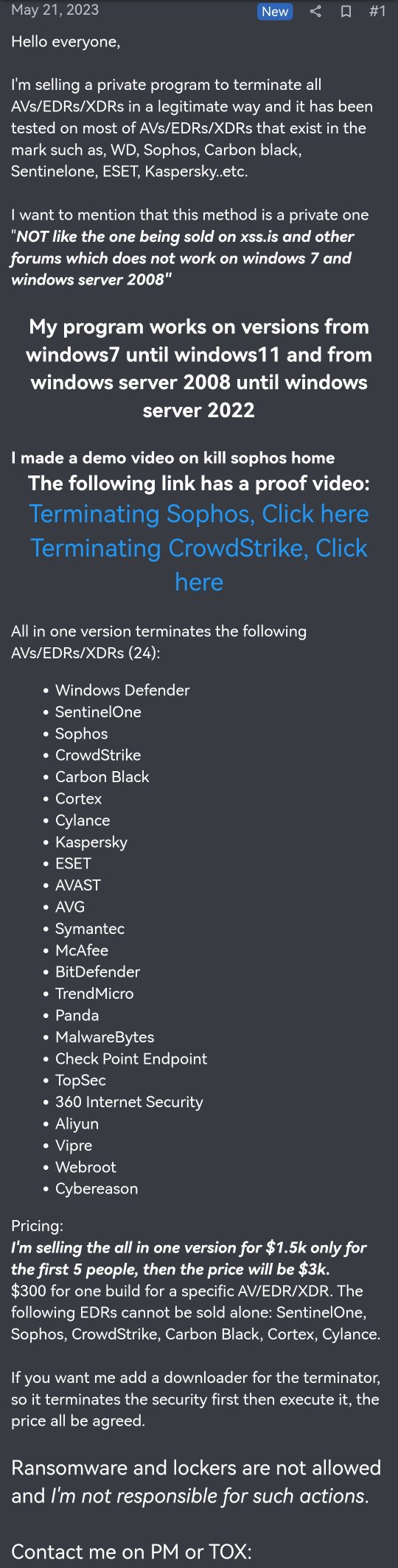
- Spyboy is a threat actor who claims to be able to terminate multiple top AV/EDR/XDR solutions. Their software, “Terminator,” is being sold over a Russian hacker forum for $300 USD for a single bypass or up to $3,000 for an all-in-one bypass of up to 23 endpoint solutions.
- The software leverages a BYOVD (bring your own vulnerable driver) approach to take over and terminate the endpoint solution using kernel-level privileges.
- Todyl’s MXDR team is carrying out continuous hunting for Terminator and other similar BYOVD and LoL (living off the land) threats. Todyl’s Endpoint Security module prevents this and other similar driver-based attacks since April of last year.
What is spyboy Terminator?
On May 21, 2023, a threat actor using the name “spyboy” began posting on a Russian-language forum known as RAMP (Russian Anonymous Marketplace). There, spyboy claimed that their software, dubbed "Terminator", could bypass nearly all AV/EDR/XDR solutions, calling out 23 vendors specifically in the post. Spyboy is currently pricing the software from $300 USD for single bypass to $3,000 USD for all-in-one bypass.
The attack seemingly first entered the public eye in a post from Twitter user Soufiane on May 28th. Around the same time, a LinkedIn post by Kaushík Pał responded to the video spyboy posted showing Terminator disabling CrowdStrike on a system.
Todyl’s timeline of events
- May 21: Spyboy begins posting about Terminator on RAMP
- May 27-present: Todyl’s MXDR Team performed a global threat hunt for signs of exploitation. Additional detections were created to actively alert on exploitation attempts to complement existing vulnerable driver exploitation prevention.
- May 28: First public mention surfaces by user Soufiane on Twitter.
- May 29: Kaushík Pał posts public LinkedIn post detailing more about Terminator and sharing a video showing spyboy disabling CrowdStrike.
- May 29: Security professionals speculate that Blackout was involved in the attack.
- May 30: Speculating security professionals on the LinkedIn post added a YARA rule to address the attack, but the rule has since been confirmed to not pertain to the spyboy software.
- May 31: CrowdStrike confirmed the activity via a post on Reddit. This post stated that their software can detect this activity with the proper settings and configurations.
- May 31: Spyboy stated that Blackout is not being used in the software despite early reports of this from the darkweb.
Drilling deeper into the attack vector
The spyboy Terminator relies on manipulating processes at the kernel level, much like other BYOVD attacks.
Admin vs Kernel Privileges
An admin user in Windows has elevated privileges compared to regular users, but they cannot directly modify kernel-level processes due to security, stability, and protection mechanisms in place. Kernel-level processes are critical components of the operating system responsible for managing system resources, and modifying them could pose security risks and destabilize the system. Windows implements privilege separation between user mode and kernel mode, with admin users operating within user mode and lacking direct access to kernel-level processes. Additionally, Windows employs protection mechanisms like Kernel Patch Protection to prevent unauthorized modifications to the kernel, and allowing arbitrary modifications could lead to compatibility issues and system instability. Specialized tools and techniques exist for kernel-level interactions, but they require specific knowledge, authorization, and adherence to strict security protocols to ensure system integrity and stability.
How Terminator works
Based on the information surfaced by the team at Todyl and the rest of the threat hunting community, here is our assessment of how Terminator works:
- Stage one: The attacker gains administrator-level privileges on an endpoint and bypasses user account controls.
- Stage two: As an admin, the attacker downloads a legitimate, signed driver file: Zemana Anti-Malware. The driver is renamed randomly and saved to the system.
- Stage three: The driver operates on the kernel level and targets endpoint security (AV/EDR) processes and terminates them.
We’ve seen this before
As stated previously, spyboy Terminator is remarkably similar to other BYOVD attacks. Threat actors have been leveraging vulnerable driver attacks for years. Most notably, the Lazarus group, the same threat actor behind the 3CX supply chain attack leveraged a vulnerable Dell driver to disable Windows monitoring capabilities.
Another notable example is the use of a vulnerable Avast Anti-Virus driver by the Cuba Ransomware group in 2021 to escalate privileges and disable malware protection. The LOLdriver project has a list of hundreds of vulnerable drivers that can be used by actors to accomplish privilege escalation, disabling anti-malware, monitoring, etc. In this case, the driver needs to be in the same directory as the Terminator executable, and the executable needs to be run as administrator.
How Todyl’s Endpoint Security defends against vulnerable driver attacks
Todyl’s Endpoint Security module, which leverages Elastic Security as a foundation, contains a YARA rule to block vulnerable driver activity on 4/4/22 to combat the original onset of BYOVD attacks. When submitting the hash from the spyboy vulnerable driver only Elastic detected it as malicious:
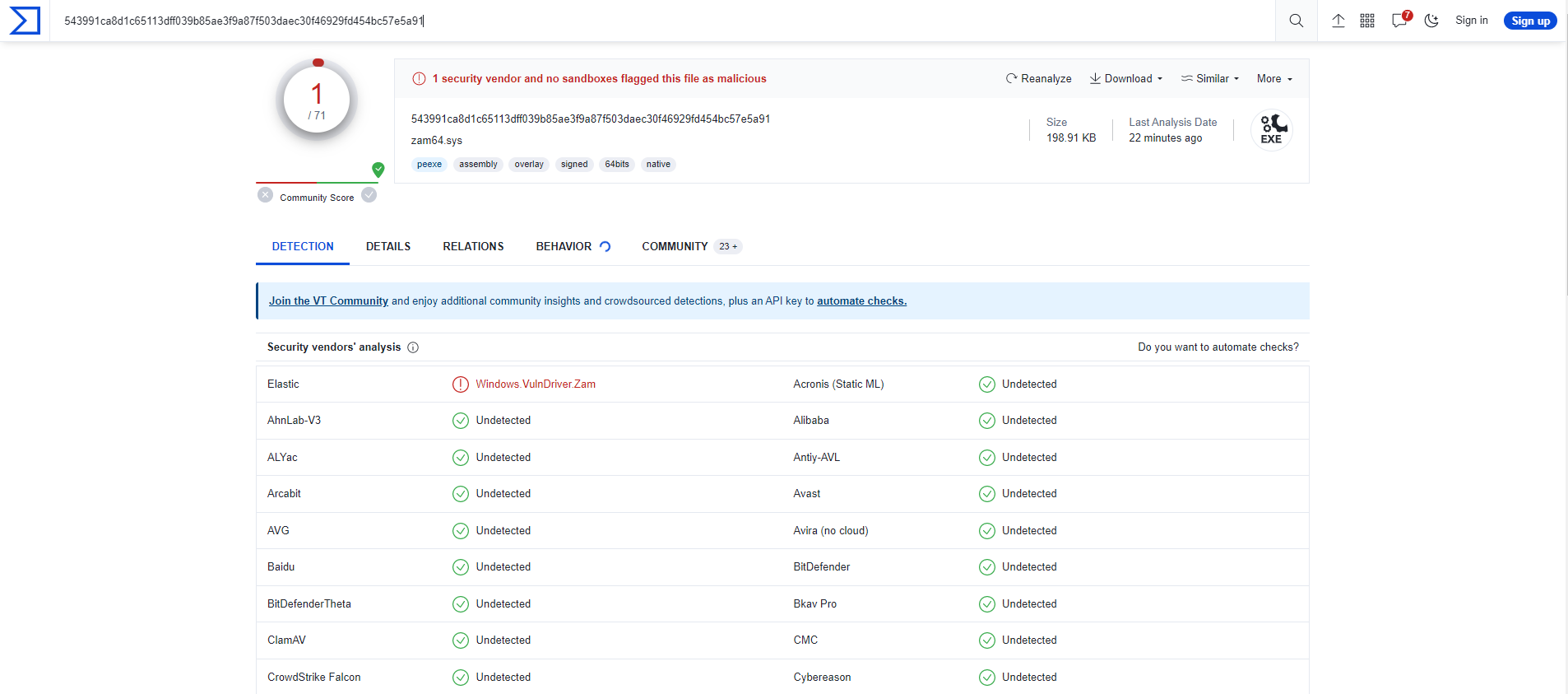
Our Endpoint Security module features signatures for vulnerable drivers, including the one used in this attack, acting as preventions against this particular attack vector.
In all cases like this, Terminator or otherwise, the first line of defense for organizations is making sure that the vulnerable driver doesn’t get on the system in the first place. Using SIEM and Endpoint Security, such as those in the Todyl platform, IT and security teams are alerted to suspicious activity. Furthermore, Todyl’s MXDR team goes a level further, investigating the activity and working to remediate it within minutes. MXDR gives customers a leg up for defending against these and many other attacks.
Recommended actions
Todyl will continue to update the community as our findings on spyboy Terminator develop, but for now, be sure to threat hunt using SIEM for IoCs. You can also use the provided hunt queries:
Additionally, check out our blog for more updates on Living off the Land and other similar attacks.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



