Threat Advisory: Business Email Compromise Campaign using OVPN for Obfuscation


Starting 8th May 2025, the Todyl Threat Research team observed the novel use of OVPN through M247 Europe SLR in Business Email Compromise (BEC) attacks. The attacks targeted a subset of our MSP partners’ tenants. M247 Europe SRL is a known host of VPN and proxy infrastructure often associated with suspicious and anonymized activity. The use of a VPN tunnel allowed the attacker to obscure their real location, blend in with other traffic, and bypass traditional geolocation-based detection mechanisms. The activity was characterized by the heavy use of Axios, a popular HTTP client for Node.js known for easy automation, scraping, and API interactions.
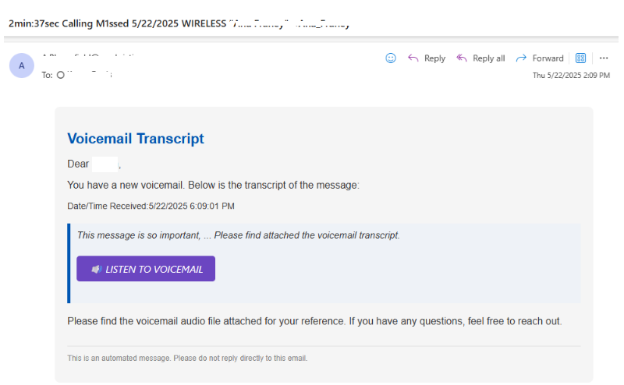

Todyl MXDR identified the attack through our existing detections and Advanced Anomaly Detection framework, using Todyl SOAR to revoke affected users’ sessions and disable their accounts for remediation. Affected partners were notified immediately of both the presence of the attack and the SOAR actions taken on their behalf.
The Todyl MXDR team has been working with our MSP partners to ensure the attackers are defeated. Our detection rules are continuously tuned to trigger alerts for BEC-related cases with critical severity to ensure our customers are protected.
Why BEC is such a threat
The FBI describes BEC attacks as one of the most financially damaging crimes out there. No complicated remote code execution required, no complex technical know-how a la hackers, and no need to chain vulnerabilities and exploit. Victims voluntarily hand over the money: what a breach of trust!
The scammer makes the email look legitimate and the tell-tale signs of it not being authentic are getting harder to spot. Hundreds of thousands of dollars have been lost in individual instances and the total loss stood at upwards of USD 55 Billion between 2013 and 2023. The estimated amount in 2024 was a staggering USD 2.8 Billion across 21442 incidents as per the FBI.
The attacks have evolved over the years:
- Emails contain more context that lures the victim into believing its authenticity
- Usage of AI has increased in crafting and targeting the messages Usage of VPN to obscure geo-location and other attributes
- Usage of malware to gain access to contextual data as well as financial account information and passwords, etc.
What You Can Do About BEC
Here's what one can do to ensure scammers don't get their way:
- Training / user education is very valuable and provides the most ROI. After all, it is all about the victim not getting scammed by figuring out that the email is not authentic
- Verify, verify, and check again
- Strong authentication, ensure MFA
- Detailed organizational policies for wire transfers and other monetary transactions coupled with strong access control
For more on ways Todyl is working to stop BEC worldwide, read our report on uncovering the Söze Syndicate.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



