A Deep Dive into SASE Static IPs


Todyl’s newest update, SASE Static IPs and SGN Routing Policies, gives users the ability to finely control egress traffic and truly make the Secure Global Network (SGN) their own. Looking through an engineering lens, adding additional steps to network processing has the potential to negatively affect performance and connectivity. Mindful of these potential drawbacks, here’s how the Todyl engineering team overcame the challenges to roll out the new SASE Static IPs and Routing Policies module.
Designing Static IPs for Performance & Control
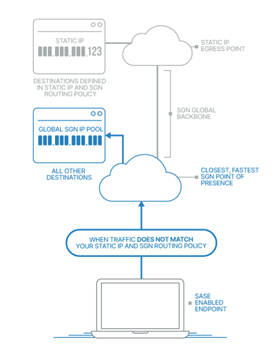
Performance is top of mind for Todyl. Our SASE is one of the fastest in the industry and we approached Static IPs through that same mindset.
Our unique Autobahn platform applies firewall rules, user-based policy, and content filtering as soon as traffic enters SASE. We added an additional step, where traffic that matches a Static IP policy is now routed across a low-latency, private backbone to the Point of Presence (PoP) with the where the Static IP address resides, increasing traffic control and optimizing latency on a global scale.
Addressing potential packet issues
A major goal of the Static IP project was to have as little impact on the underlying traffic streams as possible. One approach to routing would be to encapsulate the secure traffic within a larger packet, whose header would contain the source and destination information necessary for directing traffic across the SASE backbone. A problem with this approach is that it adds overhead to the size of the packets traversing the global network. These large packets risk exceeding maximum transmission unit (MTU) limits, causing IP fragmentation which leads to packet loss, latency, and connection instability.
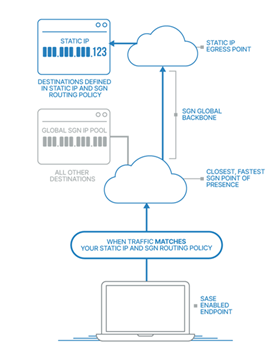
To tackle this issue, Todyl Engineering created a process where IP information is encoded when the courier receives the packet. Doing so helps identify the agent on the guardian that sent the packet as well as the Static IP source address. This maintains packet sizes and MTU values while providing the ability to route ingress traffic back to the originating source across the SGN.
Providing failover and resiliency
Another requirement for Static IP was built-in fault tolerance and load balancing. With traffic being funneled through a dedicated IP within a specific region, a lapse in connectivity could cut access to the connected resource(s) entirely.
The team built a highly redundant architecture that utilizes multiple nodes in each Point of Presence without the need for separate load-balancing hardware. Building upon the encoded routing scheme mentioned above, the team leveraged XDP (Linux eXpress Data Path) to implement a load-balancing algorithm that allows multiple nodes to receive traffic and quickly determine which device should process it. Additionally, fault tolerance was added via cross-region redundancy. In the event a specific region goes offline or is unreachable, traffic is automatically be routed to the next configured Static IP in the policy for redundancy if one is available.
More Todyl feats of engineering
Static IPs are just one of many innovations the talented team at Todyl is bringing to the cybersecurity space. Read more about the team that’s creatively solving these problems here.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



