The OneStart AI Browser Deception
Update: OneStart can be modified in functionality via updates or used to deploy other software onto the system. Recently, it's been associated with a malicious PDF editor tool, dubbed Tamperedchef. Please review our guidance for MSPs below.
Often, when a person tries to address a problem with a software solution, they will use whatever free option they can find that suits their needs in the easiest way possible. This kneejerk reaction may satisfy an immediate requirement but can open serious concerns regarding shadow IT and its cybersecurity ramifications. Without the proper vigilance and cybersecurity-first mindset, these behaviors can lead to compromise, ransomware, and breaches. For MSPs managing multiple client organizations and their users–who may be engaging in shadow IT–this concern is multiplied.
When one of our analysts flagged a suspicious scheduled task alert, we uncovered an example that perfectly illustrates why cybersecurity requires constant vigilance: the OneStart AI browser. What appeared to be a simple installation turned out to be a persistent threat that's affecting MSPs and their clients.
The Deceptive Installation Process
OneStart AI browser doesn't arrive on systems through traditional malware delivery methods. Instead, it uses a more insidious approach that makes it particularly dangerous for business environments:
- Bundled installations: The browser typically comes packaged with other third-party software that users install, particularly free PDF viewers and converters.
- Advertising disguises: It often appears leverages advertisements for websites or essential business tools as a means to lure victims into installing.
- Search hijacking: Once installed, all web searches get redirected through the browser's service before reaching Yahoo's search engine.
- Persistent presence: The software embeds itself deeply into systems, creating scheduled tasks that will reinstall it even after removal attempts.
Why This Matters for Your Security Program
Based on our analysis across customer environments, we've identified OneStart AI browser on nearly 200 different computers. Online discussions suggest this threat is widespread across organizations of all sizes, having been present for well over a month in some cases.
The browser's persistence mechanism makes it particularly problematic for business environments. Even when users or IT teams attempt to remove it, the scheduled task infrastructure ensures it returns, creating ongoing security risks and productivity impacts. This persistence creates a recurring entry point which can be used for future threat possibilities. The application also hijacks searches and consumes system resources, making it a nuisance for performance as well.
IoCs
OneStart AI browser creates several distinctive indicators that security teams can monitor:
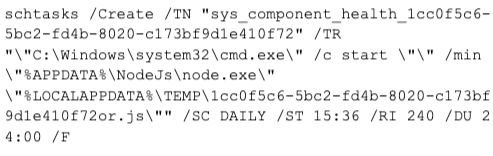
Scheduled task creation
The threat creates scheduled tasks with randomly generated names that execute Node.js from the APPDATA directory:
File system artifacts
Look for these specific file paths and patterns:
- JavaScript files ending in "or.js" in the TEMP directory
- OneStart.ai application folders in user profiles
- Scheduled tasks beginning with "sys_component_health_"
Network indicators
- DNS queries to "mka3e8.com"
- HTTPS connections to the same domain over port 443
- Node.js as the parent process for these connections
Process signers
Monitor for binaries signed by:
- OneStart Technologies LLC
- Caerus Media LLC
- Apollo Technologies Inc.
Registry key
HKCU\SOFTWARE\OneStart.ai
Folders
%LOCALAPPDATA%\OneStart.ai
Files
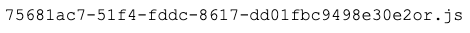
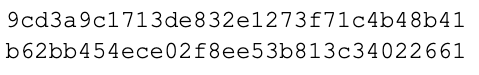
Hashes
Response and Remediation
When responding to OneStart AI browser infections, security teams should:
- Stop all processes that have OneStart in their name.
- Kill any scheduled tasks mentioning OneStart.
- Remove all files \AppData\Roaming\OneStart\" or "\AppData\Local\OneStart.ai\".
- Remove any binaries associated with the OneStart installation.
- Remove the registry entry at \software\OneStart.ai.
- Remove OneStart from \software\microsoft\windows\currentversion\run. Lessons for MSP Security Programs
This threat highlights several important considerations for MSP security programs:
- User education remains critical: Even sophisticated users can be deceived by software that appears legitimate and useful. Regular training about safe download practices and recognizing suspicious installations is essential.
- Monitoring persistence mechanisms: Traditional antivirus solutions may miss threats that use legitimate system features like scheduled tasks for persistence. Comprehensive monitoring of these mechanisms is crucial.
- Supply chain awareness: The bundling of unwanted software with legitimate tools represents a form of supply chain risk that requires ongoing vigilance.
Bottom Line
The OneStart AI browser represents the kind of persistent, deceptive threat that can slip past traditional defenses and create ongoing security risks for business environments. Although it may not steal data like traditional malware today, its ability to hijack searches, persist after removal attempts, and consume system resources makes it a legitimate concern for any security program.
MSPs who stay informed about these evolving threats and maintain robust monitoring capabilities will be better positioned to protect their clients from both traditional malware and these more sophisticated deceptive practices.
Be sure to do the following to stay ahead of threats like OneStart:
- Create a policy prohibiting the installation of non-standard browsers or unapproved PDF tools
- Regularly scan for malware using Todyl Endpoint Security and similar solutions
- Respond to cases generated in Todyl SIEM and by MXDR.
References
- VirusTotal Analysis
- Hybrid Analysis Report
- Additional Analysis
- Malwarebytes Detection
- Community Discussion
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



