VPN Vulnerabilities Rising in 2025: Are Your Networks Safe?


Virtual Private Networks (VPNs) have long been the go-to tool for secure remote access. In 2025, they occupy a strange paradox: adoption and spending are soaring, but their security reputation has never been shakier. While VPNs promise encrypted tunnels and private connectivity, they’ve also become one of the most targeted attack surfaces in cybersecurity.
For Managed Service Providers (MSPs), this presents both a challenge and an opportunity. Clients are still asking for VPNs, the market is expanding, but the vulnerabilities are stacking up. The critical question: do VPNs still make sense as the backbone of secure access, or is it time to move beyond them?
A Market That Won’t Slow Down
The global VPN market was valued at $48.7 billion in 2023 and is forecast to hit nearly $150 billion by 2030, growing at a 17.4% CAGR. Much of that demand is coming from remote and hybrid workforces, expanding cloud adoption, and rising privacy awareness.
Industry analysts point to three main drivers of this surge:
- Hybrid work is permanent. Companies need ways to connect employees to resources outside the office.
- Cloud sprawl is real. With workloads in AWS, Azure, Google Cloud, and private data centers, organizations lean on VPNs as a universal connector.
- Security optics matter. Regulators, customers, and boards expect encrypted, auditable connections. VPNs seem to check that box.
Digging deeper, VPN demand isn’t uniform. Remote-access VPNs are projected to grow faster than site-to-site deployments as distributed work remains the norm. Cloud-deployed VPNs are also gaining ground, with adoption expected to outpace traditional on-premises appliances thanks to easier scaling and management. Even consumer VPNs are booming, driven by streaming access and personal privacy concerns, though these don’t directly address enterprise risk.
The takeaway for MSPs: whether it’s a small business protecting remote staff or a mid-market organization bridging multiple clouds, VPN demand is still strong. But behind that growth is a security model stretched to its breaking point.
VPNs Under Siege: The SonicWall Lesson
If 2024 and 2025 have shown anything, it’s that VPNs are high-value targets. Attackers know that compromising a VPN gateway can open the door to entire networks.
SonicWall’s recent string of issues highlights the risk:
- Critical flaws in SSLVPN and management interfaces gave threat actors a foothold, with groups like Akira ransomware actively exploiting them.
- Legacy account migrations created credential reuse risks, allowing attackers to brute force or bypass MFA.
- Backdoors in SMA 100 appliances (the OVERSTEP malware) forced SonicWall to announce end-of-life for the product line in late 2025.
- Cloud backup breaches exposed firewall and VPN configurations, effectively handing attackers a roadmap to internal networks.
Even environments with multi-factor authentication weren’t immune. Once VPNs were compromised, attackers could pivot laterally, disable defenses, and deploy ransomware at speed.
And SonicWall isn’t alone. Ivanti Connect Secure was hit in early 2024 with multiple zero-day vulnerabilities that gave attackers unfettered access. Fortinet’s SSL-VPN has been the subject of repeated critical flaws, including CVE-2023-27997, which allowed remote code execution. Palo Alto’s GlobalProtect was also patched in 2024 after researchers uncovered a privilege escalation bug.
The message is clear: VPNs, no matter the vendor, have become one of the most reliable targets for initial access brokers and ransomware groups.
Why VPNs Are Breaking
The SonicWall saga is just a symptom of deeper structural issues. Beyond their operational disadvantages, VPNs struggle in today’s security environment because:
- They rely on implicit trust. Once inside the tunnel, users often have broad access, enabling lateral movement.
- Credentials remain king. Phished or reused passwords still unlock VPNs, even with MFA bolted on.
- They’re hard to scale securely. Patching, policy updates, and hardware upgrades leave constant gaps.
- Visibility is limited. VPNs obscure traffic, making it harder to monitor and enforce granular policies.
- Legacy hardware lingers. Unsupported appliances become easy prey.
Attackers know this. They exploit VPNs not just because of coding flaws, but because VPNs concentrate risk in a single chokepoint. A compromised VPN isn’t one cracked system: it’s a free pass into the entire network.
Put bluntly: VPNs were built for a world where “inside” and “outside” were clear. That world no longer exists.
The Post-VPN Future: SASE and Zero Trust Network Access
Although VPNs are straining under pressure, Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA) are emerging as durable alternatives. They don’t just patch VPN vulnerabilities, they reimagine secure connectivity.
Here’s how they compare:
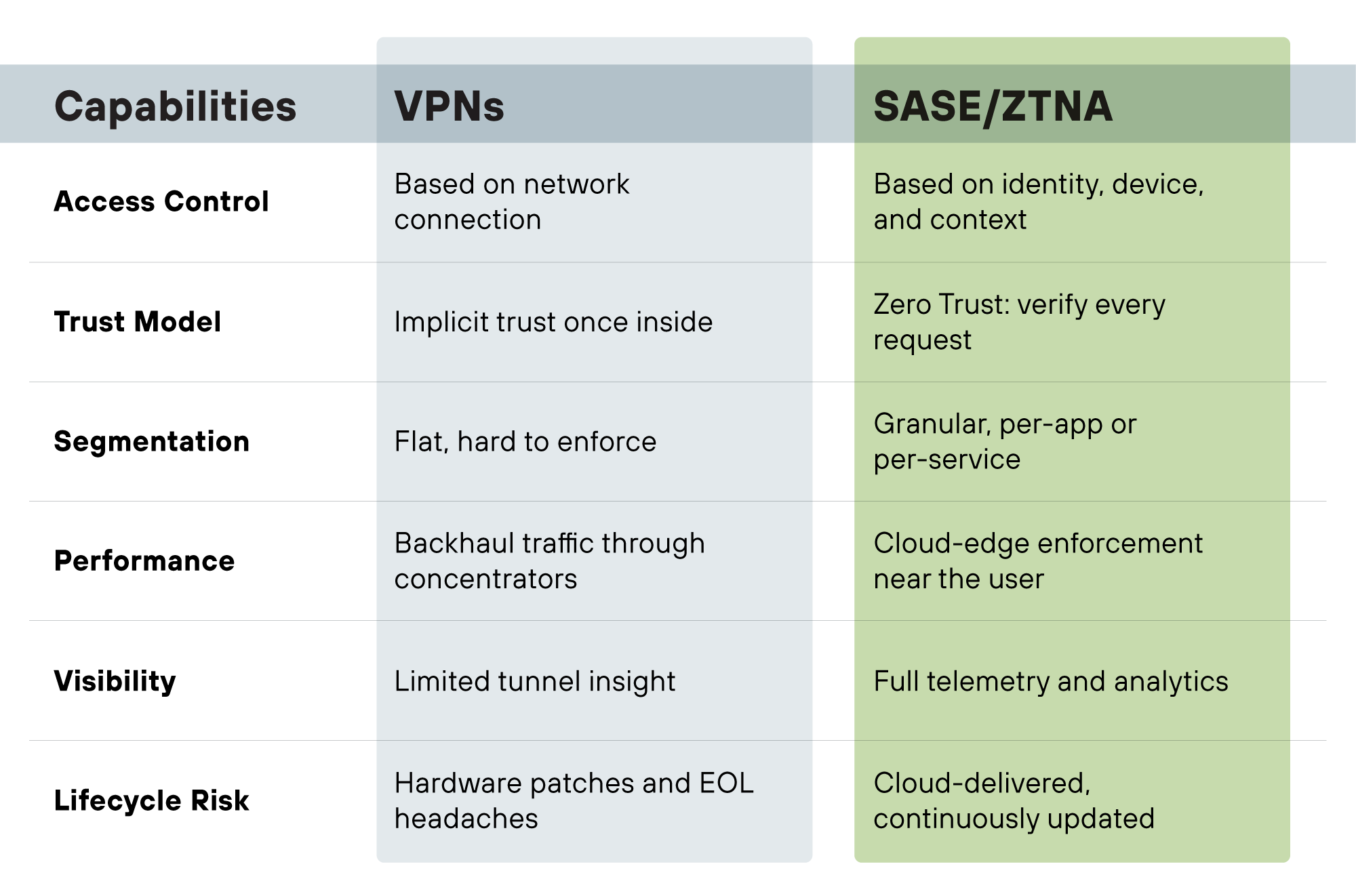
But SASE is more than “VPN plus.” It converges SD-WAN, CASB, DLP, firewall-as-a-service, threat intelligence, and more into a single cloud-delivered platform. That convergence means MSPs can reduce the number of point solutions they manage while giving clients a modern, adaptive access model.
For end users, the difference is felt in performance: no more backhauling traffic through a central VPN hub, introducing latency and bottlenecks. Instead, traffic is routed through distributed enforcement points at the edge, closer to where users and resources actually live.
What MSPs Should Do Now
For MSPs, the VPN conversation is shifting fast. Clients may still ask for them, but forward-looking providers should help chart a better course. Key steps include:
- Audit existing VPN deployments. Identify legacy appliances, unpatched endpoints, and credential risks.
- Harden where you must. Apply vendor patches quickly, rotate credentials, and restrict access to known IP ranges.
- Plan a migration path. Begin piloting SASE or ZTNA solutions with select clients, especially for cloud and SaaS apps.
- Educate clients. Position VPN vulnerabilities as a board-level risk — and frame SASE as the proactive solution.
- Phase out dependence. Maintain VPNs only where absolutely necessary, and ensure they’re tightly monitored.
Positioning the Conversation with Clients
Being security first isn’t just a way to build trust: it’s also a differentiator and a sales opportunity. SMBs and mid-market organizations often don’t realize how fragile their VPNs have become. MSPs should:
- Speak the language of compliance. Frame SASE as a way to meet evolving frameworks (like NIST 800-207 Zero Trust or CMMC requirements).
- Highlight cost efficiency. Managing VPN appliances, patch cycles, and downtime is expensive. A cloud-delivered service cuts that overhead.
- Differentiate on trust. MSPs offering SASE demonstrate forward-thinking security leadership, not just basic maintenance.
By reframing the conversation, MSPs shift from “VPN maintenance provider” to “strategic security partner.”
Conclusion: Don’t Bet Your Future on a Tunnel
The numbers say VPNs are thriving. The breaches say otherwise. In 2025, VPNs seem both indispensable and indefensible. They’re tools organizations feel like they can’t quite quit but also can’t fully trust. The truth is that VPNs are no longer the paradigm of network security like SASE is.
SASE isn’t just a VPN alternative. It’s the natural evolution. By unifying networking and security at the edge, SASE delivers on the VPN promise of secure, reliable access without the baggage of implicit trust and brittle appliances.
For MSPs, the prestige move is clear: guide clients past the VPN paradox and into a future where connectivity and security finally align. The tunnel may still exist, but the edge is where tomorrow’s access lives.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



