Akira Ransomware: Threat Assessment of a Scalable RaaS Operation


Executive Assessment
Akira is a globally active Ransomware-as-a-Service (RaaS) operation that has demonstrated sustained activity since early 2023. Rather than exhibiting victim specific tradecraft, Akira campaigns reflect a repeatable and modular intrusion model designed to scale across regions, industries, and organizational sizes.
Observed activity through 2024–2025 indicates a clear evolution toward edge driven access, credential centric lateral movement, and virtualization level impact, positioning Akira as a persistent threat to organizations with exposed remote access infrastructure and centralized compute environments.
Operational Model: RaaS Structure and Scale
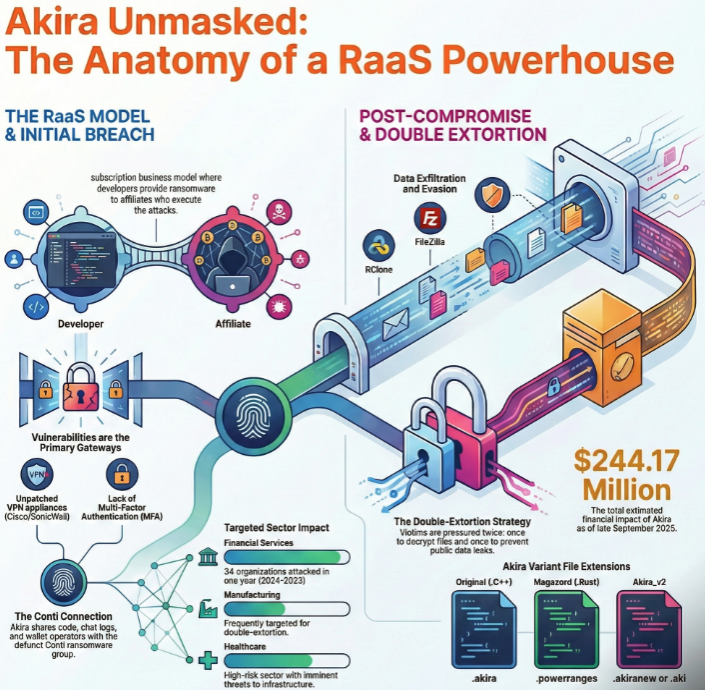
Akira operates under a distributed affiliate model, separating development and infrastructure from intrusion execution:
- Operators maintain ransomware payloads, leak sites, payment infrastructure, and negotiation services
- Affiliates independently select targets, gain access, move laterally, and deploy encryption
This structure enables parallel campaigns across multiple geographies and sectors while reducing operational risk to core developers. Disruption of individual affiliates has limited impact on overall campaign velocity.
The operation consistently employs double extortion, with data exfiltration occurring prior to encryption to maintain leverage regardless of backup maturity.
Initial Access Trends: Edge Infrastructure as Primary Vector
Threat intelligence reporting and incident response observations indicate Akira affiliates strongly favor internet facing remote access infrastructure, particularly VPN appliances, as initial access vectors.
Recurring access patterns include:
- Exploitation of SonicWall SSL VPN vulnerabilities, including CVE-2024-40766
- Targeting of Cisco VPN infrastructure, such as CVE-2023-20269
- Abuse of compromised, reused, or legacy credentials
- Use of credentials obtained via initial access brokers
Affiliates demonstrate rapid weaponization of newly disclosed vulnerabilities, often exploiting them within short timeframes following public disclosure, suggesting active vulnerability monitoring rather than opportunistic scanning alone.
Post Access Behavior: Rapid Internal Expansion
Following initial access, Akira intrusions tend to prioritize speed and coverage over long term stealth. Across multiple investigations, the time between access and domain level control frequently ranges from hours to several days.
Observed behaviors include:
- Active Directory enumeration using built-in tooling and frameworks such as Impacket
- Credential access via Kerberos abuse rather than LSASS dumping
- Lateral movement using RDP, SMB, WinRM, SSH, and commercial remote access tools
The reliance on valid credentials and native protocols significantly reduces malware artifacts during early stages, complicating detection through signature based controls.
Virtualization and Infrastructure Targeting
A defining evolution in Akira’s tradecraft is its increasing focus on virtualized environments. While early campaigns primarily impacted Windows systems, later activity expanded to:
- Linux based environments, including VMware ESXi
- Hyper-V infrastructures
- Nutanix AHV virtual machine disk files (observed in 2025 activity)
By encrypting VM disk files or targeting hypervisors directly, affiliates can disable large numbers of systems simultaneously, increasing operational disruption and recovery complexity. This shift aligns with a broader ransomware trend toward infrastructure level impact rather than host by host encryption.
Data Exfiltration and Extortion Mechanics
Prior to encryption, Akira affiliates routinely stage and exfiltrate data using legitimate tools, including:
- Rclone
- WinSCP
- File transfer clients such as FileZilla
Exfiltrated data volumes vary but commonly range from hundreds of gigabytes to multi-terabyte datasets, depending on dwell time and access scope. Centralized leak infrastructure allows operators to standardize extortion messaging across victims.
Tooling and Payload Evolution
Akira ransomware payloads have undergone incremental technical refinement:
- Transition from C++ to Rust based encryptors
- Configurable encryption options, including partial file encryption to increase speed
- Pre-encryption process termination to release file locks
- Active removal of backup artifacts, including Volume Shadow Copies and third-party backup software
These changes suggest optimization of a mature codebase rather than experimental development.
Threat Outlook
Akira should be assessed as a persistent, medium to high sophistication threat with strong operational consistency. Its effectiveness is driven less by novel malware and more by systemic weaknesses: exposed edge services, credential sprawl, and insufficient monitoring of internal authentication and virtualization layers.
The operation’s reliance on affiliates and valid credentials indicates continued adaptability as long as these conditions persist.
Mitigations and Detection Considerations
Edge and Identity Hardening
- Prioritize patching of VPN and remote access appliances, especially SonicWall and Cisco devices
- Enforce phishing resistant MFA on all external access and administrative accounts
- Audit and remove legacy or dormant credentials, particularly post upgrade VPN accounts
Credential and Lateral Movement Detection
- Monitor for anomalous Kerberos activity (e.g., unusual ticket issuance, service account misuse)
- Alert on unexpected use of Impacket related techniques and tooling patterns
- Baseline RDP, SMB, WinRM, and SSH usage to identify deviations in volume or source
Virtualization Security
- Segment hypervisor management interfaces from general user networks
- Monitor access to VM disk files and unexpected VM power-state changes
- Apply security updates to hypervisors and virtualization management platforms promptly
Data Exfiltration Controls
- Monitor outbound data transfers for large or sustained uploads using common exfiltration tools
- Restrict use of file transfer utilities on servers where not operationally required
Backup and Recovery Resilience
- Maintain offline or immutable backups isolated from domain credentials
- Regularly test recovery from hypervisor level backups, not just endpoint restores
Closing Assessment
Akira is not defined by a single exploit or campaign, but by a repeatable operational pattern that scales across environments. Its continued success highlights the gap between security control deployment and effective visibility into identity, edge, and infrastructure layers.
From a threat intelligence perspective, Akira should be monitored less as a discrete malware family and more as an ecosystem of access methods, affiliates, and infrastructure aware attack paths that are likely to persist and evolve.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



