ClickFix: The Evolution of Copy-Paste Social Engineering


Executive Summary
ClickFix represents a highly effective social engineering technique that exploits user trust and legitimate system interfaces to achieve initial compromise. First observed in October 2023, this attack method convinces victims to manually execute malicious commands by copying and pasting content into the Windows "Run" dialog box or terminal, effectively circumventing traditional security controls designed to prevent automated execution.
The sophistication of ClickFix campaigns has evolved dramatically since their inception. Modern variants leverage trusted brand identities, employ JavaScript injection to populate clipboard contents automatically, and have expanded beyond Windows to target macOS and Linux systems. By exploiting the human element rather than technical vulnerabilities, threat actors have created an attack vector that remains effective even against organizations with robust endpoint security.
Key characteristics of ClickFix attacks include:
- Social engineering focus: Exploits user behavior and trust rather than technical vulnerabilities
- Evasion capabilities: Bypasses traditional security solutions by leveraging legitimate system tools and processes
- Rapid adoption: Multiple threat actor groups and APT organizations have incorporated this technique since mid-2024
- Server-side controls: Threat actors implement IP blacklisting, geographic filtering, and bot detection to evade security research and analysis
What's New? Recent Developments
ClickFix Becomes the Dominant Initial Access Vector
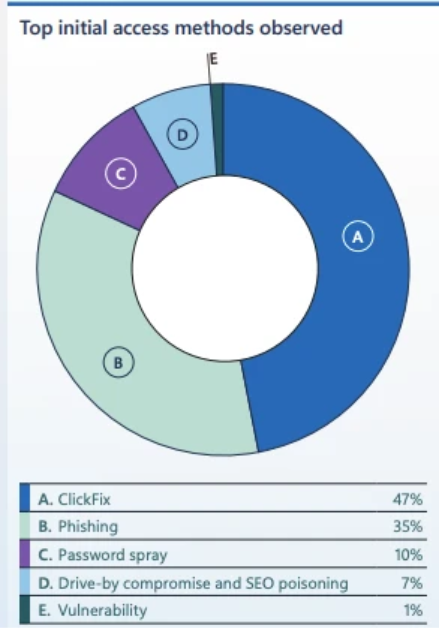
Microsoft's 2025 Digital Defense Report revealed that ClickFix emerged as the most prevalent initial access method in 2025, representing 47% of observed attacks. This dramatic surge demonstrates how rapidly threat actors have adopted and scaled this technique across their operations.
Advanced Cloudflare-Themed Social Engineering
Modern ClickFix campaigns increasingly leverage fake Cloudflare bot verification pages, which have become ubiquitous across the legitimate web. These sophisticated lures include several enhancements designed to maximize victim compliance:
- Dynamic OS detection: Commands automatically adapt based on the victim's operating system (Windows, macOS, Linux)
- Instructional videos: Embedded video tutorials demonstrate exactly how to execute the malicious commands
- Social proof indicators: Fake counters displaying "users verified in the last hour" and countdown timers create urgency and authenticity
- Professional design: High-fidelity replicas of legitimate Cloudflare interfaces that are nearly indistinguishable from authentic verification pages
As noted by Push Security researchers: "It almost looks like Cloudflare shipped a new kind of bot check service. The embedded video, countdown timer, and counter for 'users verified in the last hour' all serve to increase the sense of authenticity, and put extra pressure on the victim to complete the check."
Blue Screen of Death (BSOD) Impersonation
Threat actors have begun weaponizing one of Windows' most recognizable error screens. These attacks use full-screen browser windows to display convincing BSOD replicas that include malicious "recovery" commands. Victims, believing their system has crashed, follow the displayed instructions to "restore" their computer, unknowingly executing the attacker's payload.
Fake Windows Update Screens
Building on the BSOD concept, attackers have also developed fake Windows Update interfaces that mimic the familiar blue update screen. These displays instruct victims to execute commands to "complete" or "accelerate" the update process, leveraging users' familiarity with legitimate Windows update procedures that sometimes require system intervention.
FileFix: The Next Evolution
FileFix represents a significant evolution of the ClickFix technique, moving the attack vector from the Run dialog to Windows File Explorer. Instead of copying PowerShell commands, victims are instructed to paste malicious file paths or commands directly into the File Explorer address bar, leading to malware execution through file system manipulation.
Cache Smuggling: Invisible Payload Delivery
A particularly insidious development uses cache smuggling techniques. In these attacks:
- Victims visit a compromised or malicious website that appears to display benign images or content
- Malicious payloads are embedded within image files or other seemingly harmless content and stored in the browser cache
- JavaScript code later retrieves these cached files, via a typical clickfix attack, and extracts the hidden malicious code
- The payload executes without triggering traditional download-based detection mechanisms
This technique effectively bypasses security controls that monitor network traffic and file downloads, as the malicious content technically arrived through a previous, apparently benign web request and is retrieved locally from cache.
Recent Notable Attacks
PhantomCaptcha: Geopolitical Targeting
Security researchers uncovered PhantomCaptcha, a sophisticated spearphishing operation targeting Ukrainian government agencies and international NGOs, including the Red Cross and UNICEF. The campaign employed the following methodology:
- Victims received convincing fake Zoom meeting invitations via email
- Links directed targets to credential-harvesting sites displaying fraudulent CAPTCHA verification prompts
- The "verification token" victims were instructed to copy and paste actually contained PowerShell commands
- Successful execution installed a WebSocket-based Remote Access Trojan (RAT) capable of real-time system control and data exfiltration
This campaign demonstrates how ClickFix techniques have been adopted by APT-level threat actors for geopolitically motivated operations.
TikTok "Activation Guide" Scams
A viral ClickFix campaign spread rapidly through TikTok, leveraging the platform's algorithm to reach millions of potential victims. The scam purported to offer:
- Free Windows activation keys and commands
- Cracked Microsoft 365 licenses
- Adobe Photoshop activation bypasses
- Fake Spotify Premium subscriptions
Videos instructed viewers to copy and execute commands that appeared to activate these services but instead installed information stealers, cryptocurrency miners, and remote access tools. The campaign's virality was amplified by teenagers and young adults sharing the videos with friends, believing they were distributing helpful software hacks.
KongTuke Campaign: Widespread Web Compromise
The KongTuke campaign represented a mass-compromise operation affecting thousands of legitimate websites:
- Attackers compromised WordPress sites, content management systems, and poorly secured web servers
- Injected malicious JavaScript created fake CAPTCHA verification prompts on infected pages
- Visitors attempting to access legitimate content were presented with ClickFix-style lures
- Multiple payload variants were observed, including information stealers and banking trojans
Researchers also documented a FileFix variant within this campaign that deployed a PHP-based RAT through Windows File Explorer manipulation, demonstrating the attackers' technical sophistication and willingness to employ multiple attack vectors simultaneously.
From Obscure Technique to Mainstream Threat
APT Adoption
The effectiveness of ClickFix has attracted attention from nation-state threat actors. Security researchers have observed multiple Advanced Persistent Threat (APT) groups incorporating ClickFix-style lures into their operational toolkits, including:
- MuddyWater (Iranian APT): Integrated ClickFix techniques into spearphishing campaigns targeting Middle Eastern government and critical infrastructure organizations
- APT28 (Russian GRU): Employed ClickFix lures in operations against European government entities and defense contractors
This adoption by sophisticated state-sponsored groups validates the technique's effectiveness against even security-conscious targets and suggests ClickFix will remain a persistent threat for years to come.
Commercialization and Commoditization
The underground cybercrime economy has rapidly commoditized ClickFix capabilities. Specialized builders and "ClickFix-as-a-Service" offerings are now readily available on dark web forums and Telegram channels:
Basic packages ($200-$500):
- Pre-built phishing page templates
- Simple command obfuscation
- Basic CAPTCHA and error message themes
Premium subscriptions ($1,000-$1,500/month):
- Professional Cloudflare and reCAPTCHA template designs
- Multi-language support for international targeting
- Anti-analysis features (VM detection, geographic filtering, researcher IP blacklists)
- Automated obfuscated command generation
- Real-time campaign statistics and victim tracking dashboards
- Regular template updates to evade detection
- Customer support and customization services
This commercialization has dramatically lowered the technical barrier to entry, enabling low-skill cybercriminals to execute sophisticated social engineering campaigns. The availability of turnkey ClickFix tools ensures this threat will continue proliferating across the threat landscape.
The Future of ClickFix
Blurring Execution Boundaries
The next evolution of ClickFix attacks will likely continue blurring the distinction between code executing locally on the victim's system and code running within the browser sandbox. This convergence creates detection challenges:
- WebAssembly exploitation: Using WASM to perform malicious operations that bridge browser and system contexts
- Progressive Web Apps (PWAs): Abusing PWA capabilities to gain persistent access and expanded permissions
- Browser extension manipulation: Tricking users into installing or enabling malicious browser extensions through ClickFix-style social engineering
- Clipboard API abuse: Exploiting browser clipboard access to pre-populate commands without user visibility
- Cross-platform scripting: Developing universal payloads that detect and adapt to any operating system environment
AI-Enhanced Social Engineering
As artificial intelligence becomes more accessible, threat actors will likely leverage generative AI to create hyper-personalized ClickFix campaigns:
- Dynamic content generation based on victim profiling
- Real-time conversation simulation in chatbot-style lures
- Automated translation for global targeting without language barriers
- Voice and video deepfakes integrated into instructional content
Existing Detection Rules
Todyl's Security Platform includes multiple detection rules specifically designed to identify ClickFix attacks:
ClickFix RunDLL32 Execution for Stage 1
Detects when a ClickFix attack leverages rundll32.exe to execute a remote DLL payload, a common technique for initial stage execution that loads additional malware components.
ClickFix PowerShell Download for Stage 1
Identifies when a user executes a PowerShell command containing ClickFix-associated phrases such as "I am not a robot reCAPTCHA" or "I am Human" through the Windows Run dialog, indicating a social engineering compromise.
ClickFix MSHTA Download for Stage 1
Detects MSHTA-based ClickFix attacks where victims paste commands invoking Microsoft's HTML Application host to download and execute malicious scripts or applications.
ClickFix Windows Run Dialog Misuse for Stage 1
Monitors suspicious modifications to the Windows RunMRU (Most Recently Used) registry key, which records commands executed through the Run dialog and often contains forensic evidence of ClickFix attacks.
Learn more
For more information on ClickFix being stopped in the wild, read this piece on how our team uncovered an attack live.
For similar breakdowns and threat coverage, read more threat intelligence from Todyl’s research team.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



