BECs In the Wild: When Millions of People Are Expecting the Same Email
Tax season. Black Friday. Back to school. These aren't just busy times for your business; they're prime hunting season for cybercriminals to take advantage of when executing Business Email Compromises(BECs) and similar attacks. Bad Actors know that when everyone's inbox is flooded with expected messages about the same topic, people let their guard down. And few corporate events are as universally anticipated, or as ripe for exploitation, as the annual benefits open enrollment period.
Every fall, employees across the country expect emails about health insurance, 401(k) changes, and benefits deadlines. It's the perfect cover for a phishing attack. Threat actors craft convincing messages that look like they're from HR or your benefits provider, complete with urgent deadlines and links to "update your information." One distracted click by any employee and you’re compromised.
This isn't a theoretical threat. Todyl’s MXDR team recently detected and shut down a sophisticated phishing campaign that did exactly this—exploiting the end-of-year open enrollment window to target organizations with highly credible fake benefits emails. Here's how it unfolded, how we caught it, and what it means for your security posture.
Rapid Detection and Response Saves Organizations
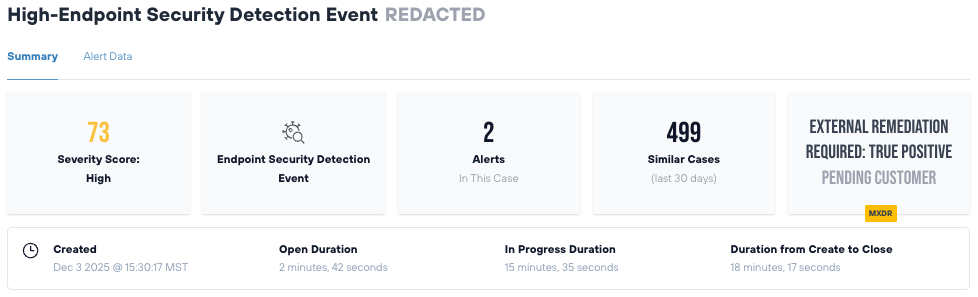
Response Metrics
Time to Investigation: 2 minutes, 42 seconds
Time to Containment: 15 minutes, 35 seconds
Total Case Duration: 18 minutes, 17 seconds (from creation to close)
Result: Threat neutralized in under 20 minutes from initial alert, preventing potential data exfiltration, lateral movement, and business disruption.
Event Timeline
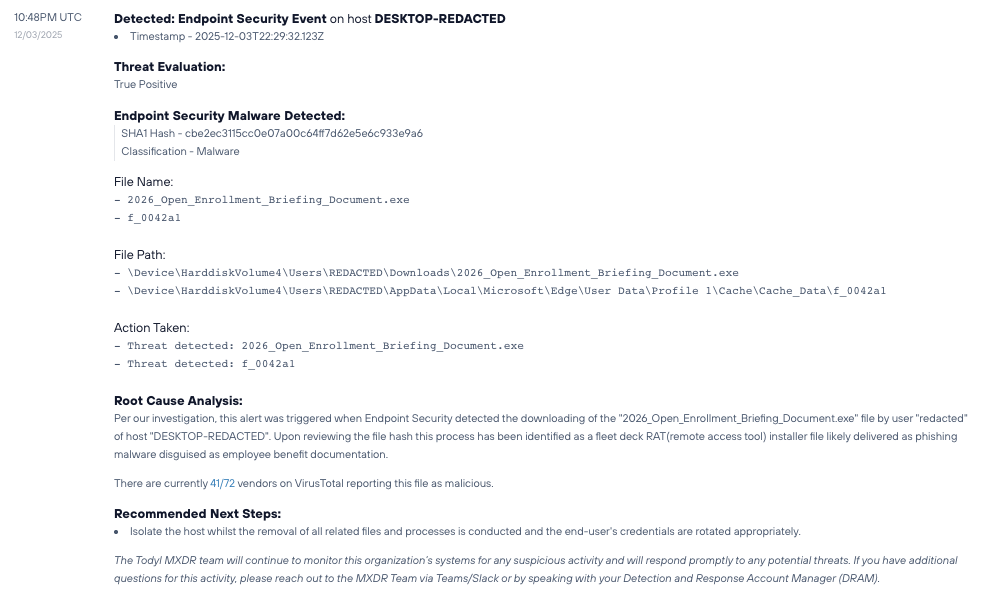
~3:14 PM - User receives and opens a phishing email in Outlook containing a malicious link
3:14:26 PM - User clicks embedded link, which launches Microsoft Edge and redirects through a malicious domain (redirecting-v6md[.]vercel[.]app)
3:14:42 PM - (16 seconds later), malicious file "2026OpenEnrollmentBriefing.msi" downloaded (94.1 MB actual / 4.19 MB compressed)
3:14:42 PM - Todyl detects the attempted RAT (Remote Access Trojan) execution immediately
3:15:30 PM - MXDR case automatically created by Todyl platform
3:18:12 PM - Security analyst begins investigation (2 minutes, 42 seconds after case creation)
3:33:47 PM - Threat contained and case closed
Sandbox Analysis Revealed:
Upon execution in a controlled environment, the malware exhibited sophisticated evasion and social engineering tactics:
Evasion Technique #1 - File TypeManipulation:
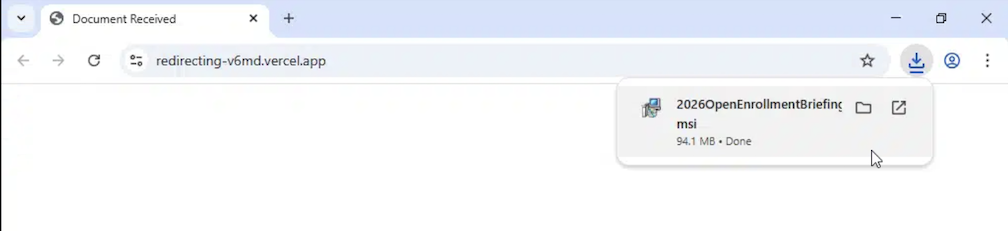
- Initially delivered as"2026OpenEnrollmentBriefing.msi" (Windows Installer package)
- MSI files are often trusted by browsers and EDR solutions as legitimate software installers
- This format bypasses many file scanning mechanisms that focus on .exe files
Evasion Technique #2 - Code Signing Abuse:
- Digitally signed with valid certificate from "FLEETDECKINC." (Sectigo CA)
- CertificateIssuer: Sectigo Public Code Signing CA EV R36
- Valid from:July 19, 2024 to July 19, 2027
- Thumbprint: CA172BACE97F7C97A6AE9E16CC9360F59E7B9CF4
- TriggeredUAC prompt displaying "Verified publisher: ITarian LLC"
- Leveraged trust in legitimate security/management software branding
- Used dual-identity confusion (FleetDeck/Comodo Security Solutions/ITarian) to maximize victim trust
- BECs In the Wild: When Millions of People Are Expecting the Same Email
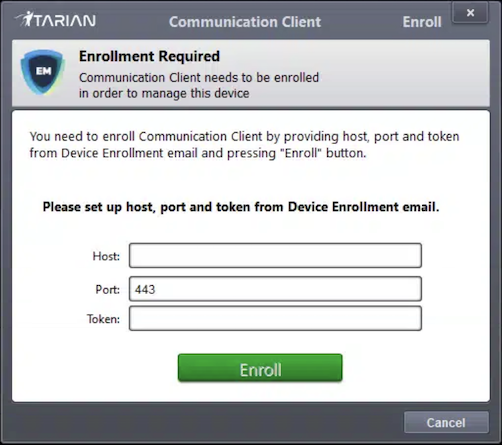
EvasionTechnique #3 - Interactive C2 Setup:
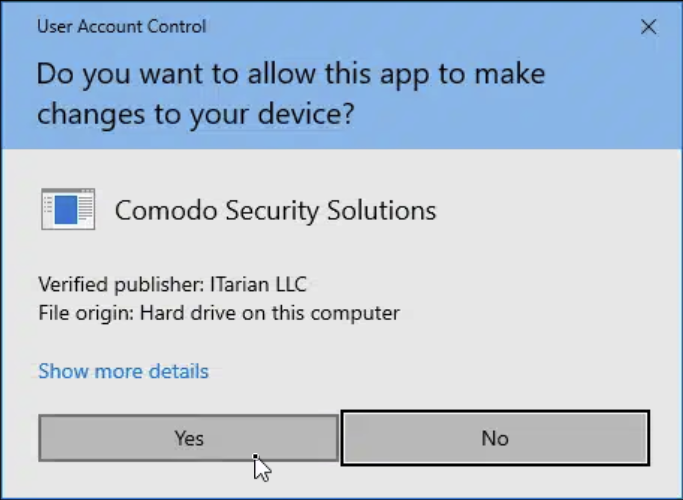
- Deployed an"ITarian Communication Client" requiring enrollment
- Attempted to establish persistent command-and-control connection
- Used port443 (HTTPS) to blend with legitimate traffic
- Required victim to manually configure C2 connection parameters (host/port/token)
- Manual enrollment step designed to evade automated sandbox detection systems
The Bottom Line: Your Best Defense is Being Prepared
Business email compromise attacks are only getting more sophisticated and even the best-trained employees can slip up. Attackers know that open enrollment season, tax deadlines, and other routine events create the perfect cover for exploiting lax security measure and inattentive users. That's why layered security and rapid detection and response capabilities are essential.
At the end of the day, it's not about being paranoid, it's about being prepared. When attackers come after your users, you want to shut them down before they can do any damage. The right combination of solutions like SASE, SIEM, endpoint protection, and 24/7 detection & response can give you the tools you need to protect your environment and dramatically reduce your risk.
Stay vigilant. Stay protected. And if you need backup, we're here to help.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



