Threat Advisory: New IcedID Trojan Campaign


On November 17, 2022 Todyl’s MXDR team observed new infections from a campaign that included the IcedID Trojan, first discovered in 2017 by IBM X-Force[1]. This new activity targets users in the US with IRS notifications and file names such as IRS_Form_11-17-2022_16-48-39.exe. These infections differ from the Emotet activity seen by Proofpoint[2] in recent weeks because the actor used a re-registered parked domain to host the malware.
Newly registered domain
The threat actor re-registered the domain name www-irs-gov[.]com on 11-17-2022. The domain appears to have been registered and re-registered with several registrars since 2015:
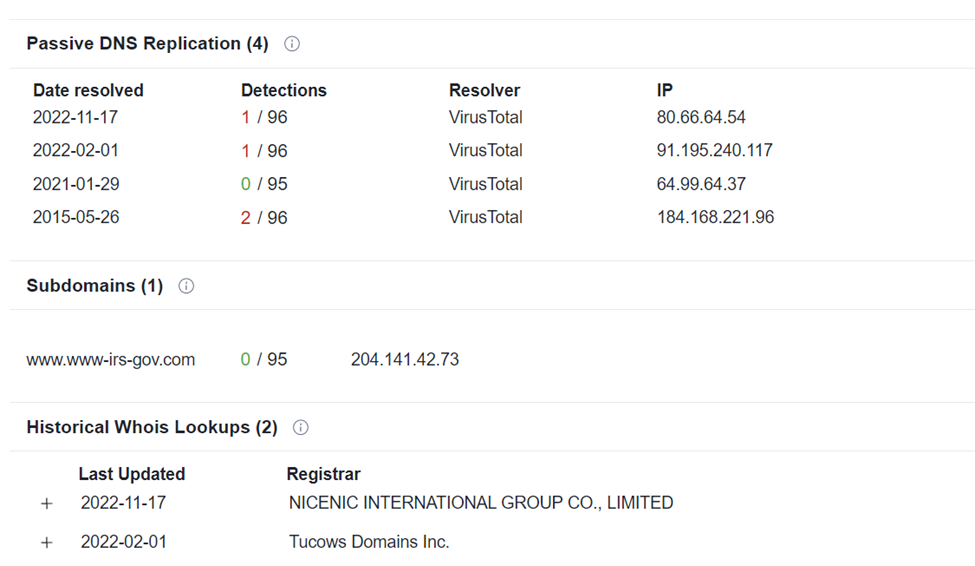
At the time of writing, the domain is associated with the IP 80[.]66[.]64[.]54, a web server that has several domains associated with it that have been created in and first seen in the last week. Based on the domains and subdomains, the actor seems to be attacking Australian targets as well.
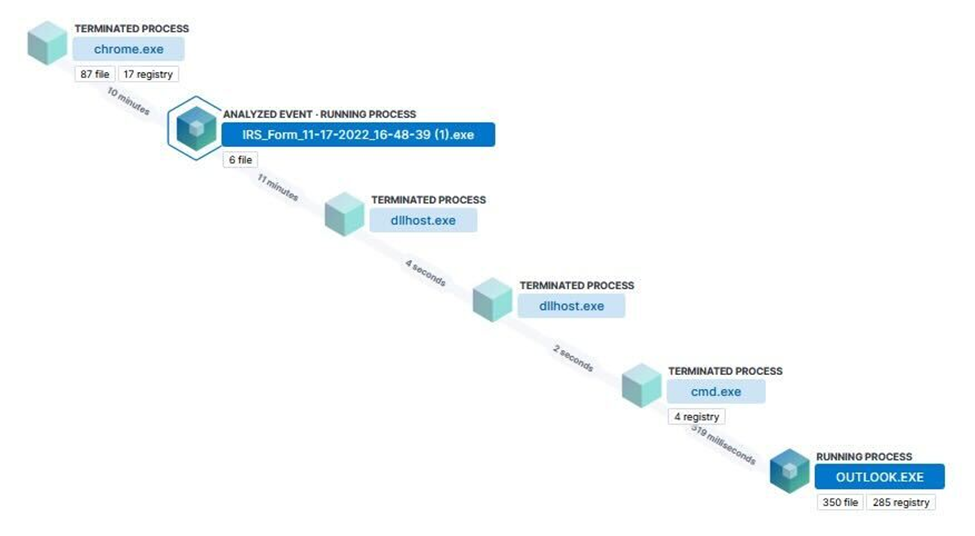
Executable behavior
Upon running, the executable performs a memory injection into an unbacked executable section and utilizes rundll32.exe to load a dropped dll (Abuyafpt.dll) that creates a scheduled task via svchost.exe. Multiple .tmp files are then dropped in the temp folder and it is observed that dllhost.exe launches cmd.exe that opens outlook.exe.
- process.threat.Ext.start_address_module: "C:\Users\{users}\Downloads\IRS_Forms_11-17-2022_16-48.39.exe"
- Target.process.threat.Ext.start_address_module: "Unbacked"
- process.command_line: "cmd.exe /c start "" outlook.exe"
- process.parent.command_line: "C:\Windows\system32\svchost.exe - k netsvcs - p -s Schedule"
- process.command_line: "rundll32.exe "C:\Users\{user}\AppData\Roaming\User-1\User-1\opyacn.dll",#1 - damuib="DebateAlcohol\license.dat""
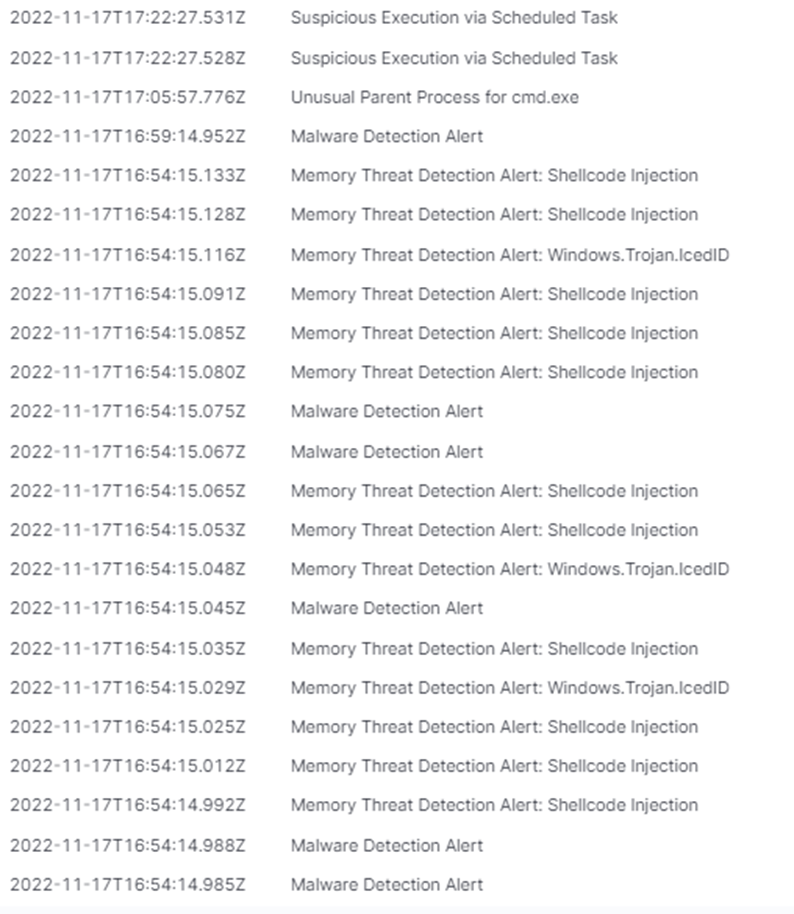
Detection mechanism(s)
The Todyl Security Platform’s Endpoint Security (EDR + NGAV) and Managed Cloud SIEM capabilities utilized several detection methods including:
- Memory Threat Detection: Shellcode Injection
- YARA Signatures for the IcedID Malware
- Malware Detection
- Unusual Parent Process for cmd.exe
- Suspicious Execution via Scheduled Task
Activity such as this illustrates the need for a comprehensive security platform that not only looks at the endpoint, but also pulls in correlation data to a SIEM from Network, DNS, and Proxy, among others.
Indicators of compromise
Associated with malware:
- www-irs-gov[.]com
- 80[.]66[.]64[.]54
- IRS_Form_11-17-202_16-48-39.exe - e5af30f751cb20f72b4a127d2bb075477659148ed8af047b97f4263d46bc132
- barrelx64.tmp - 2374f26dfa20f1697f089d017e3d5f2138f07c240e35b358ce71f6d99c2f2ea3
- Abuyafpt.dll - a3ca4733682bc3e5a5b28f6815b5d13375a7ddaead45654b23f9bc1466f914b8
- opyacn.dll - 19c772133e924c89c9a149cdc697226fc8697f3bbf839df5f8c135aab0b5cf85
- $RWW6XP7.exe - e5af30f751cb20f72b4a127d2bb075477659148ed8af047b97f4263d46bc1328
- C:\Users\{user}\AppData\Roaming\user-1\Abuyafpt.dll
- C:\Users\{user}\AppData\Roaming\DebateAlcohol\license.dat
Associated with threat actor infrastructure:
- www-irs[.]com
- sdr-nb[.]com
- wwww-dlscord[.]com
- trackitem[.]link
- moralaz[.]top
- acridpanel[.]com
- dpd-trackit[.]uk
- ksd-ir[.]com
- thm-ve[.]com
- servicesaustralia[.]gove[.]au[.]thm-ve[.]com
- dpd-trackit[.]link
- www[.]servicesaustralia[.]au[.]csk-io[.]com
- servicesaustralia[.]gov[.]au[.]thm-ve[.]com
- csk-io[.]com
- gov[.]au[.]csk-io[.]com
- au.csk-io[.]com
Update: November 18, 2022
The Todyl MXDR & Adversary Threat Intelligence (ATI) teams continue to monitor the situation with the IcedID campaign. After examining the Portable Executable (PE), we were able to find other indicators associated with the campaign: asiksliopakt[.]com.
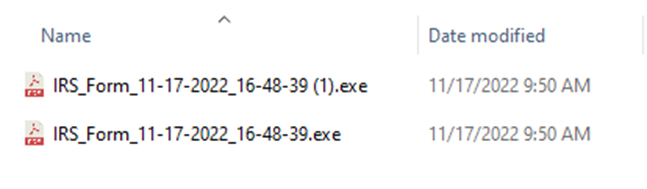
PE Details
The file shows as a PDF if the end-user is hiding file extensions, which is default in Windows, thereby tricking the user into thinking they are opening a PDF as opposed to running a malicious binary.
Looking at the strings, we can tell the file is packed. Using our Endpoint Security solution, we can essentially unpack it by viewing the compressed bytes from the shellcode injection alert.

Copying the bytes into CyberChef, we can create a recipe to decompress the bytes.
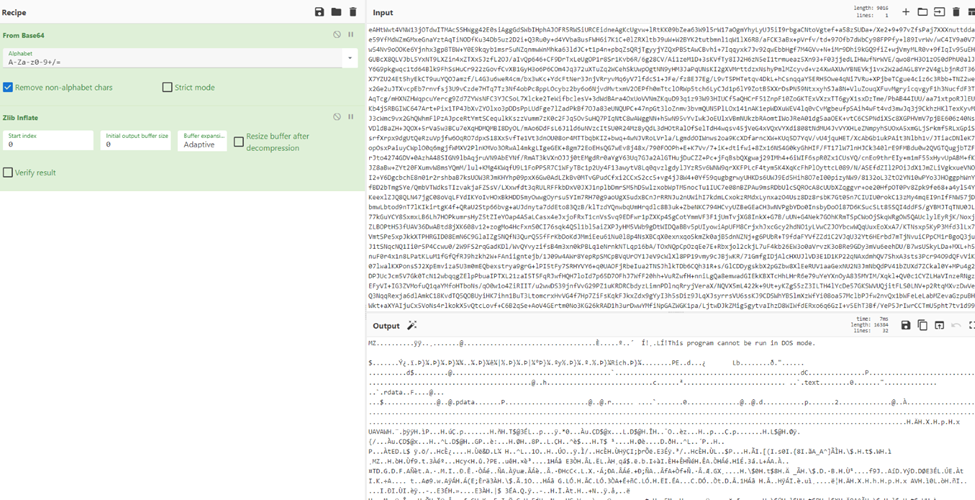
After decompressing the bytes, we can see the MZ header that indicates the PE file type. We then saved the decompressed file as iced.dat and ran it through Elastic's IcedID extractor tool [3].
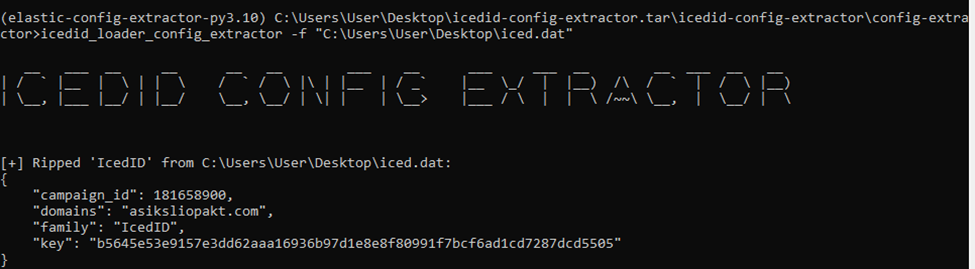
This provides the threat actor's campaign ID, domain, and XOR key:
"campaign_id":181658900
"domains": "asiksliopakt.com"
"family": "IcedID",
"key": "b5645e53e9157e3dd62aaa16936b97d1e8e8f80991f7bcf6ad1cd7287dcd5505"
Todyl's layered protection with our Threat Intelligence feeds has proactively blocked this indicator for partners. Additionally, we added all indicators we identified to our blocklist.
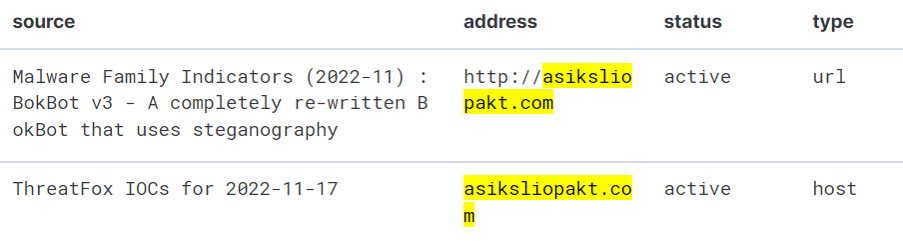
The actor seems to have multiple campaigns targeting different geographic locations as evidenced by the graph below:
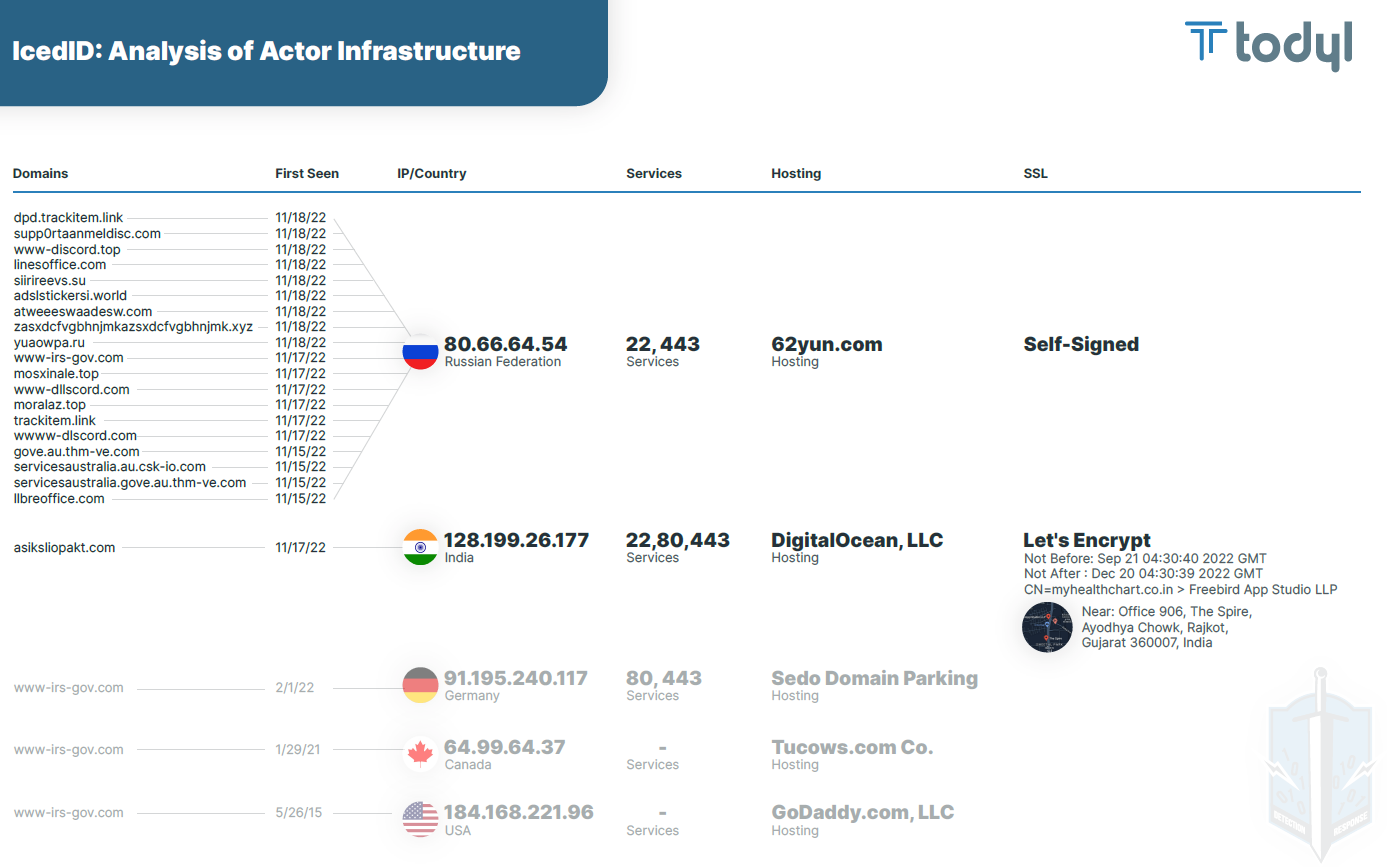
Timeline of events
Below is a timeline of events we've observed associated with this threat actor:
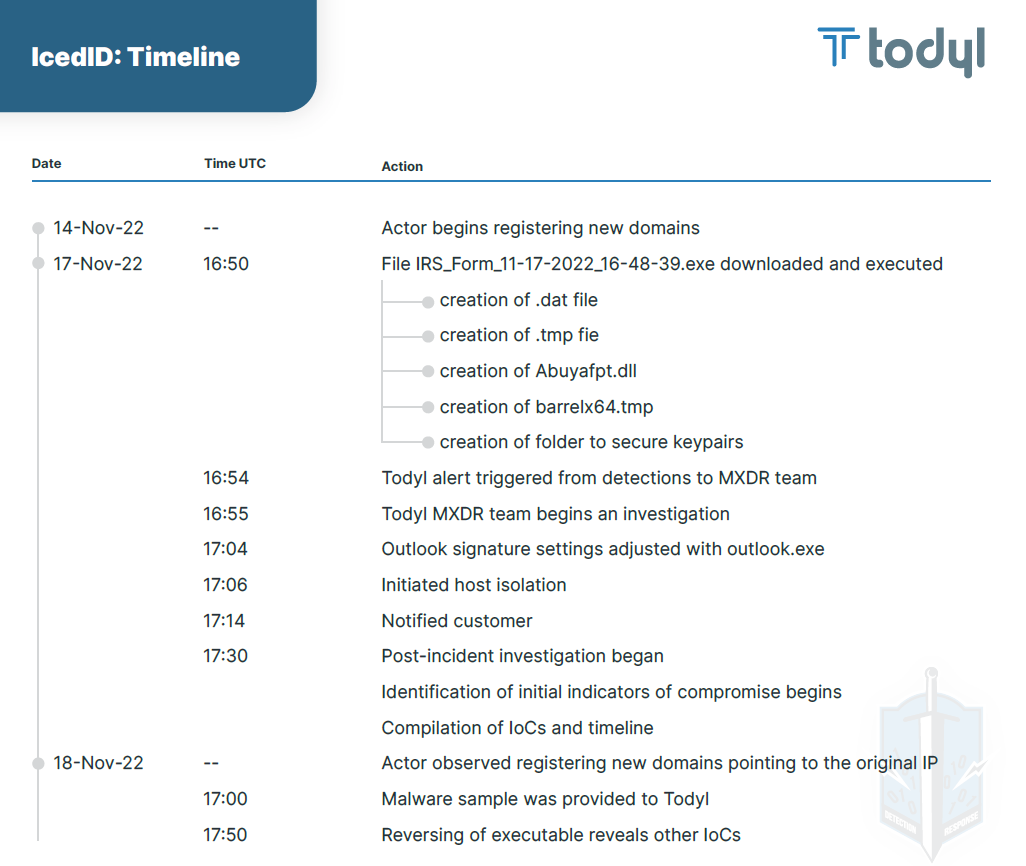
Since this is a fluid, developing campaign, we will continue to update this blog as we acquire and confirm additional information.
Key takeaways
- Defense-in-depth is key. Only one of the domains had a valid public certificate. Todyl's SASE Proxy with SSL Inspection would block communication by default for traffic using self-signed certificates. SSL inspection is paramount, blocking self-signed certificates will mitigate some threats and cause actors to go after low hanging fruit.
- The threat actor used a wide variety of hosting across multiple continents to potentially evade geographic network level controls.
- The threat actor is demonstrating an elevated level of sophistication and operational capabilities as indicated by nightly builds to change hashes and avoid detection.
- Companies need a holistic solution to get full protection from threats, simply focusing on Endpoint or Network and vice versa is not enough to detect and respond to evolving threats.
- What's old is new again, threat actors will use parked domain names and aged out threat indicators to launch new campaigns, causing red herrings and threat teams to go "we've seen this before"
- Actors who go "dormant" may just be planning their next move
Additional IoCs
Attributed to binary
- asiksliopakt[.]com
Associated with threat actor
- dpd.trackitem[.]link
- supp0rtaanmeldisc[.]com
- www-discord[.]top
- linesoffice[.]com
- siirireevs[.]su
- adslstickersi[.]world
- atweeeswaadesw[.]com
- zasxdcfvgbhnjmkazsxdcfvgbhnjmk[.]xyz
- yuaowpa[.]ru
- mosxinale[.]top
References
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



