Preparing for CMMC Level 1: What Your Organization Needs to Do


Does your organization or clients work with the Department of Defense (DoD) or other federal organizations/contractors? If so, then attaining Cybersecurity Maturity Model Certification (CMMC) Level 1 compliance is essential to your business operations.
There is ambiguity surrounding what CMMC entails and who is subject to it, which we hope to clarify. This blog is the first in our guide series on CMMC, outlining why you would need to consider CMMC Level 1 and exactly what you need to do to prepare for it.
CMMC Level 1: What it is and who needs it
The CMMC program is a cybersecurity assurance framework issued by the DoD that sets forth contractual requirements for contractors and subcontractors who process, store or transmit government-controlled information. The framework is organized into three certification levels, each aligned with the sensitivity of the information handled:
- Level 1 (Foundational) for organizations handling only Federal Contract Information (FCI)
- Level 2 (Advanced) for those handling Controlled Unclassified Information (CUI)
- Level 3 (Expert) for the most sensitive defense-related data
Why it matters
The DoD’s website confirms that the program will begin implementation on November 10, 2025, when the first phase of self-assessments will become applicable in relevant contracts.
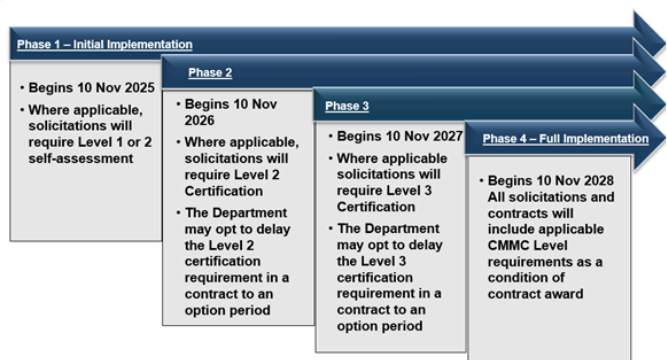
Ensuring compliance with CMMC matters because the DoD is now making cybersecurity a condition of contract award rather than simply a good practice. Beginning November 10, 2025, solicitations and contracts will start including CMMC requirements based on the level required by the contract’s data sensitivity. Organizations that fail to meet the appropriate level will risk ineligibility for DoD contracts.
At Level 1, which is the entry point for firms handling only FCI, organizations must implement foundational cyber-hygiene practices and perform an annual self-assessment. By taking proactive action toward Level 1 readiness, organizations protect their ability to compete for DoD business and demonstrate baseline cyber-resilience.
The 17 required practices at Level 1
Here are the practices your organization must cover, organized into six domains:
Access Control (AC)
- Limit system access to authorized users, processes and devices.
- Limit the types of transactions and functions that authorized users can execute.
- Verify and control connections to external (non-organizational) information systems.
- Control information posted or processed on publicly accessible systems.
Identification & Authentication (IA)
- Identify information system users, processes acting on behalf of users, devices.
- Authenticate (or verify) identities of users, processes or devices before granting access.
Media Protection (MP)
- Sanitize or destroy information system media containing FCI before disposal or reuse.
Physical Protection (PE)
- Limit physical access to systems, equipment and operating environments to authorized personnel.
- Escort visitors and monitor their activity when in areas containing sensitive information.
- Maintain audit logs of physical access.
- Manage physical access devices (e.g., keys, cards, biometric readers) and control their use.
System & Communications Protection (SC)
- Monitor, control and protect communications at the external boundary and key internal boundaries of the information system.
- Separate publicly accessible systems from internal systems by physical or logical means.
System & Information Integrity (SI)
- Identify, report and correct system flaws in a timely manner.
- Employ malicious code protection mechanisms and update them timely.
- Update malicious code protection mechanisms.
- Perform periodic system scans and real-time scanning of files from external sources.
Step-by-step preparation guide
Here’s a prescriptive, action-oriented checklist for organizations to get ready for Level 1:
- Confirm applicability: Determine whether your organization is part of the Defense Industrial Base, handles FCI and has or expects DoD contracts with CMMC language. If so, Level 1 either applies, or serves as a baseline for higher levels.
- Map the required practices: Create a document listing all 17 practices. For each practice, identify:
- Which systems/devices/processes are in-scope (those processing, storing or transmitting FCI)
- Who is responsible for each practice
- Current state (fully implemented / partially / missing)
- Conduct a current-state assessment: Using the mapping, for each of the 17: confirm whether the required control exists, how it is enforced, and what evidence supports it.
- Identify and remediate gaps: For any practice marked “partially” or “missing” implement the controls required. Prioritize remediation of the biggest gaps that impact your ability to demonstrate compliance.
- Prepare for self-assessment: Since Level 1 certification is achieved via an annual self-assessment:
- Schedule the assessment (assign a senior official to affirm compliance)
- Collect and store evidence (logs, configuration records, policies, training records) showing each practice is met.
- Decide whether you’ll perform internally or engage a third-party to assist (which is still a self-assessment, not a third-party certification).
- Document the self-assessment and affirmation: Conduct the assessment, mark each practice as MET/NOT MET/N/A, document findings, and obtain the senior official’s affirmation. Retain the self-assessment report and evidence for review by primes or DoD as required.
- Maintain compliance year-round: Because the self-assessment is annual, your organization should maintain continuous compliance; monitor changes, update documentation, and reassess whenever systems or contracts change.
- Flow-down and supply-chain awareness: If you subcontract or use suppliers, ensure that your supply-chain partners meet their obligations regarding FCI and CMMC Level 1 practices (and higher levels if applicable).
Contract and timeline implications
- The DoD is phasing in CMMC requirements in new solicitations; be prepared for CMMC clauses to appear in contracts.
- Being ready for Level 1 gives you eligibility to bid on contracts that require at least basic cyber hygiene; delays may reduce your competitiveness.
Achieving Level 1 readiness is not optional if you plan to continue working with the DoD and handle FCI. The practices are straightforward but must be documented and continuously maintained.
Use the mapping, gap analysis and self-assessment steps above to get ahead. If you handle higher sensitivity data (CUI), then you’ll need to look beyond Level 1, but this foundational work still serves you well.
To learn more regarding other Level 1 considerations, and the other levels of CMMC, read our eBook, Understanding the CMMC Program.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



