Threat Advisory: Email Account Compromise


Amidst recent rises in business email compromise (BEC) campaigns, the Todyl Threat Research team has uncovered a similar emerging threat: email account compromise, or EAC.
What is Email Account Compromise (EAC)?
EAC is a specific subset of BEC, relying on full account takeover (ATO) as a means for attacking an organization from within. In an EAC scenario, an attacker first gain access to an individual’s email account through:
- Social engineering/phishing attacks
- Brute force attacks like password spraying
- Purchasing credentials through initial access markets
Once inside, the real attack begins, shifting into BEC. The bad actor uses emails, calendar invites and meetings, company directories, and shared files to study the victim and develop an understanding of who they are and how they operate. Attackers will even build forwarding rules to ensure a constant flow of information, tweaking account permissions to avoid detection and maintain access.
Once they understand their victim, the attacker assumes their identity. They will mimic the user’s behavior, sending emails and responses in a timely manner, making them almost indistinguishable from the victim. This differs from other BEC approaches that use spoofing and other detection tactics to trick people into thinking something is legitimate. Instead, the attacks come directly from a legitimate account, controlled by a bad actor like a puppet.
The Use of AI in EAC and BEC
Artificial intelligence is already being used to create convincing wording for phishing and other BEC campaigns, but it takes an even more sinister turn in the case of EAC. Specifically, AI deepfakes and voice cloning now give attackers even more ways to fully impersonate EAC victims. The result is even more convincing mimicry, making it difficult for blue teams to discern that an account is compromised.
Todyl’s Findings
While defending our partners, the Todyl Threat Research team noticed a few key commonalities across EAC cases like this one.
Inbox rules
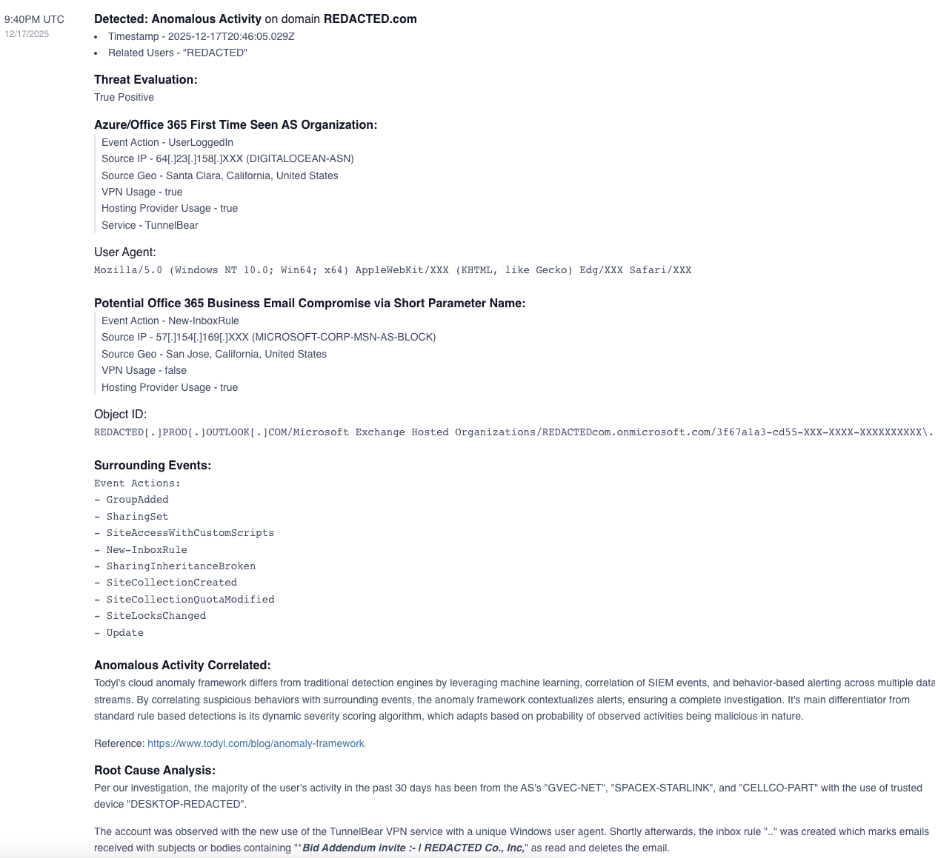
As discussed earlier, inbox forwarding rules are often used in EAC attacks to obscure an attacker’s activity. Specifically, our teno thankam found that a bad actor will use these rules to hide emails they have sent as the victim. For example, an attacker will move a sent email to lesser used folders such as the RSS or Conversation History folders. That way, they can use these emails for other BEC attacks without losing record of conversations for maintaining their victim profile.
Attackers will determine where to route these emails based on the information gathered in their initial reconnaissance. One scenario would be a user who rarely if ever checks their Spam or Junk folders. The attacker’s emails can be stored there, hiding in plain sight, and then automatically deleted after 30 days, leaving no trace.
Although not definitive, our team noticed that these rules will usually be named with 1-3 characters, such as:
- ?
- ??
- ...
- ....
- ,,,
Email deletion
According to our team’s findings, more active/enterprising attackers will take a step further. Instead of rerouting sent emails to an unused folder, they will actively delete the email from Sent, and then quickly remove it from the Deleted Items folder as well. This removes any apparent evidence of their activity, leaving the victim none the wiser.
Here is an example case:
How to Defend Against EAC
Because attackers go to great lengths to hide their activities, detecting and stopping EAC can be difficult. Amongst the cases we’ve seen so far, here are a few prevailing trends to look for within your SIEM:
- Email logins at unusual hours
- Logins from unusual or foreign locations (geolocation)
- Impossible Travel
- Unusual user-agent
- ASNs with a bad reputation
- VPNs with a bad reputation
- IPs with a bad reputation
- Multiple failed logins and then a success (also brute force from multiple IPs)
- MFA Bypass
You can also search for abnormal forwarding rules, especially ones with naming conventions like those detailed above. Other potential signs of this type of account compromise include:
- RSS Feeds folder activity
- Volume of emails being sent out exceeds normal threshold per day/hour/minute
- Emails being sent out at unusual times (after midnight and before 6am)
- Sending an email and then deleting it out of Sent Items in less than a minute
How Todyl can Help
Thanks to the efforts of our Threat Research team, the Todyl Platform is already tuned to detect these indicators of compromise to help you root out and stop potential EAC threats. With Microsoft Entra ID and Google Workspace integrations, Todyl helps you uncover and address email-based threats quickly to prevent EAC from happening within your environments.
To learn more, contact us to see how you can get started proactively defending yourself and your clients from these threats. You can read what other new and emerging threats our team are tracking—and how to stop them—on our threat intelligence feed.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



