Cybersecurity Action Month
It's time to move from awareness to action
You and your clients are already aware. What's needed now is action.
Business email compromise attacks are evolving, threat actors are targeting firewalls and VPNs directly, and the holiday season is when threat actors increase activity. Todyl helps MSPs move from cybersecurity awareness to unified threat, risk, and compliance management to defend against increasing threats.
If you are in the first 50 MSPs that book a demo and attend, you'll get a free signed copy of Eric O'Neill's latest book, Spies, Lies, and Cybercrime: Cybersecurity Tactics to Outsmart Hackers and Disarm Scammers.
Take Action Today - Book a Demo


Attend a demo, get a signed copy of Eric O'Neill's new book!
In his latest book, Spies, Lies, and Cybercrime, national security strategist and former FBI counterintelligence operative Eric O’Neill exposes how nefarious cybercriminals relentlessly attempt to access your data and wallet, and arms you with his proven tactics for spotting and neutralizing cyberthreats to protect yourself, your family, and your business.

5 Steps to Strengthen Your Client's Security Before the Holidays
1. Deploy Identity Threat Detection & Response for BEC protection
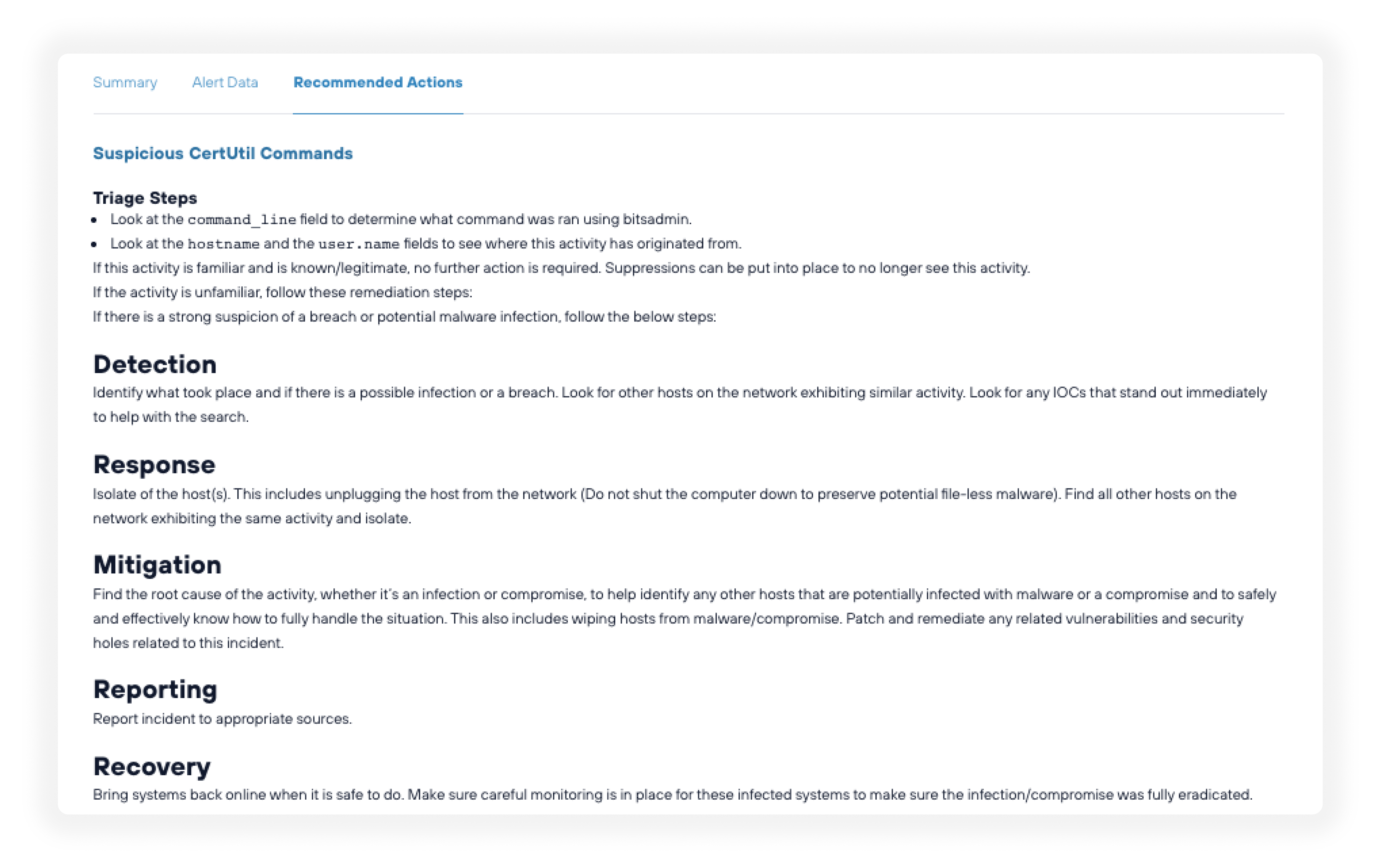
BEC attacks exploit compromised credentials to impersonate executives, redirect payments, and steal sensitive data from Microsoft 365 and Google Workspace environments. Todyl MXDR teams respond to attempted BEC attacks in an average of 2 minutes.
Todyl MXDR includes Identity Threat Detection & Response (ITDR) for 24/7 monitoring of anomalous identity usage. When something looks wrong, our team investigates and responds. You get a named Detection and Response Account Manager who works as an extension of your team.
2. Reduce attack surface area with SASE & Zero Trust Network Access
Traditional VPNs create security gaps and user experience problems. Once an attacker gains VPN access, they can move laterally across your clients' networks. Partners save around $6K annually by eliminating VPN infrastructure.
Todyl SASE with Zero Trust Network Access gives users seamless, secure connections from anywhere. Your clients get modern security that actually improves their team's experience.
3. Deploy advanced Endpoint Security
Ransomware, fileless malware, in-memory attacks, and advanced persistent threats target endpoints as the entry point for compromise.
Todyl EDR and NGAV uses behavioral analysis and machine learning to stop threats before they execute. Partners report 81% reduction in false positives, which means less noise and more focus on real threats
4. Gain comprehensive visibility and precise threat detection across endpoint, network, and cloud
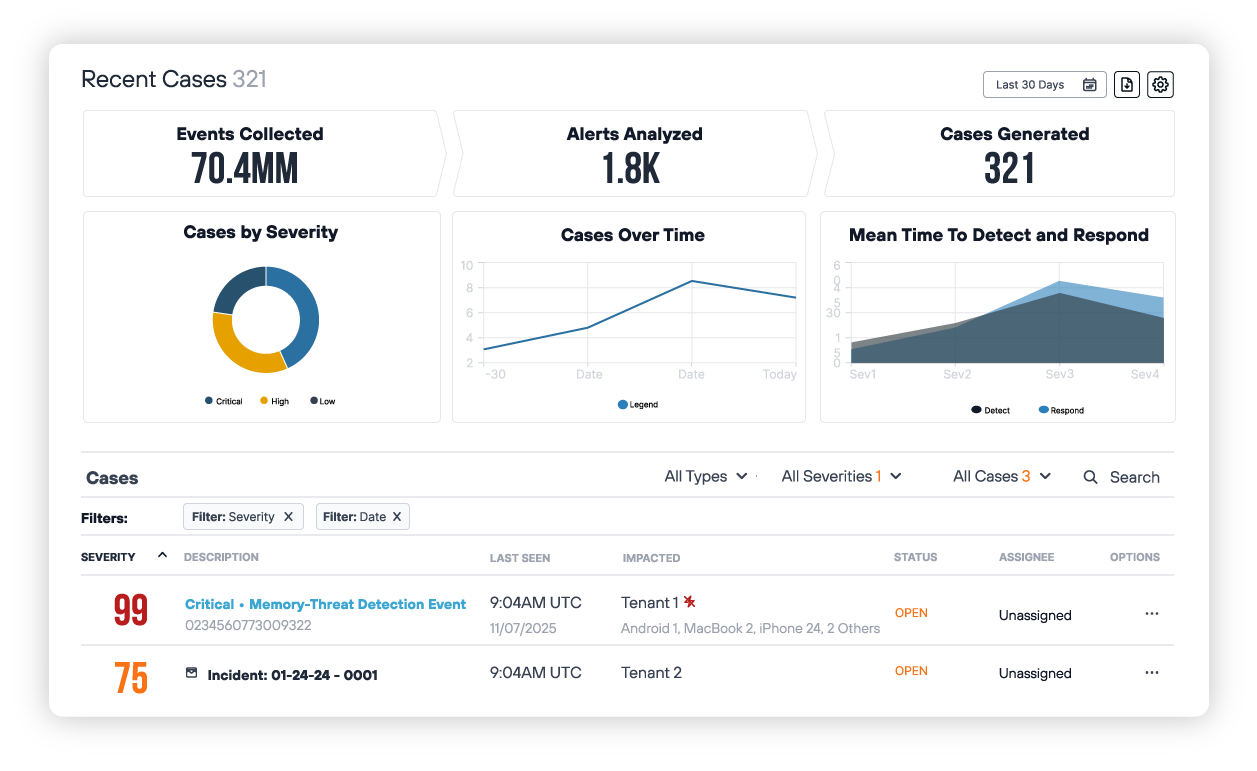
Fragmented security tools create blind spots. Without unified visibility, threats go undetected and compliance becomes nearly impossible to demonstrate. Partners report 99% improvement in visibility after consolidation.
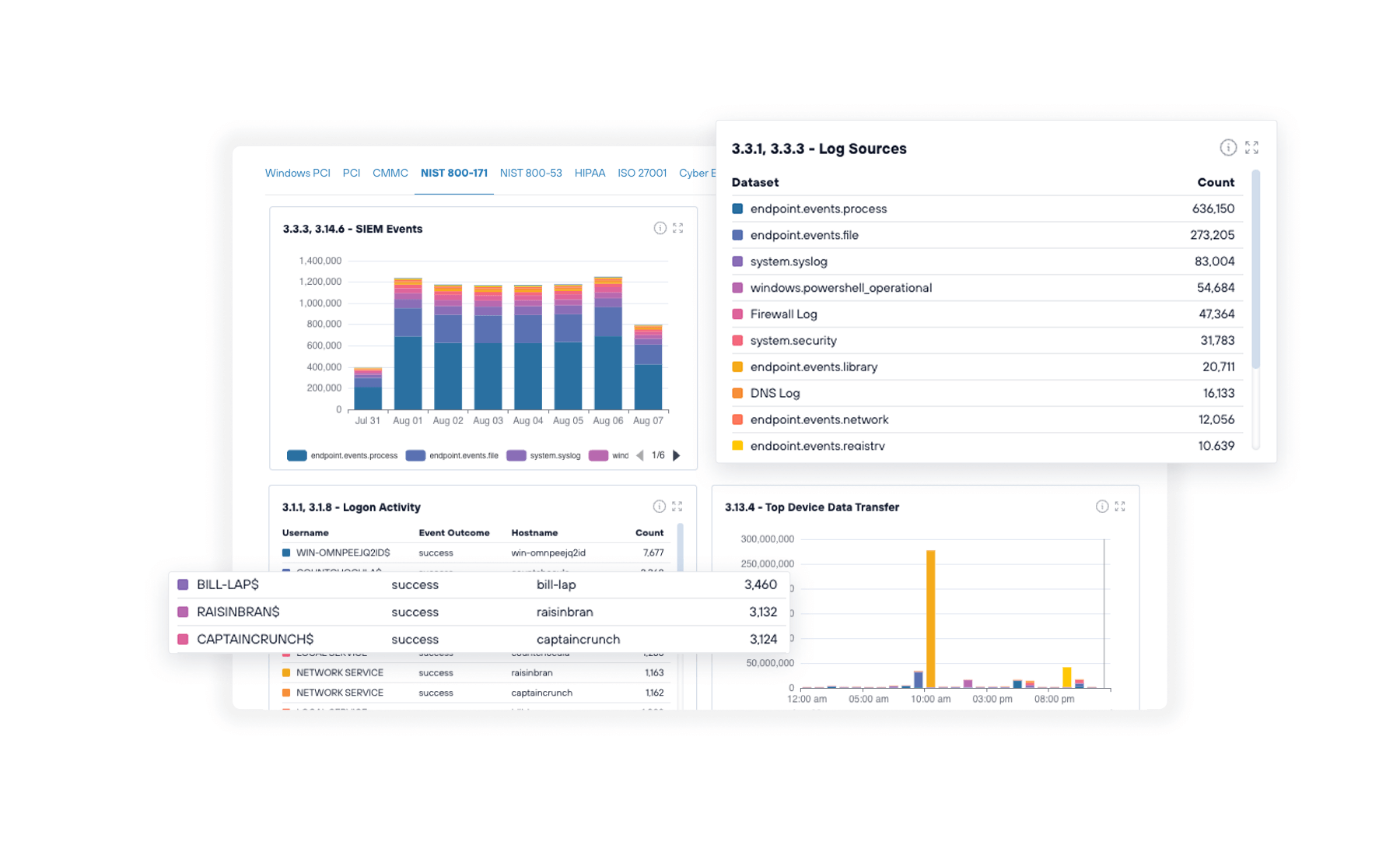
Todyl SIEM consolidates security data into one platform with advanced analytics and automated correlation. You get real-time anomaly detection across endpoints, networks, and cloud environments with faster response when something needs attention.
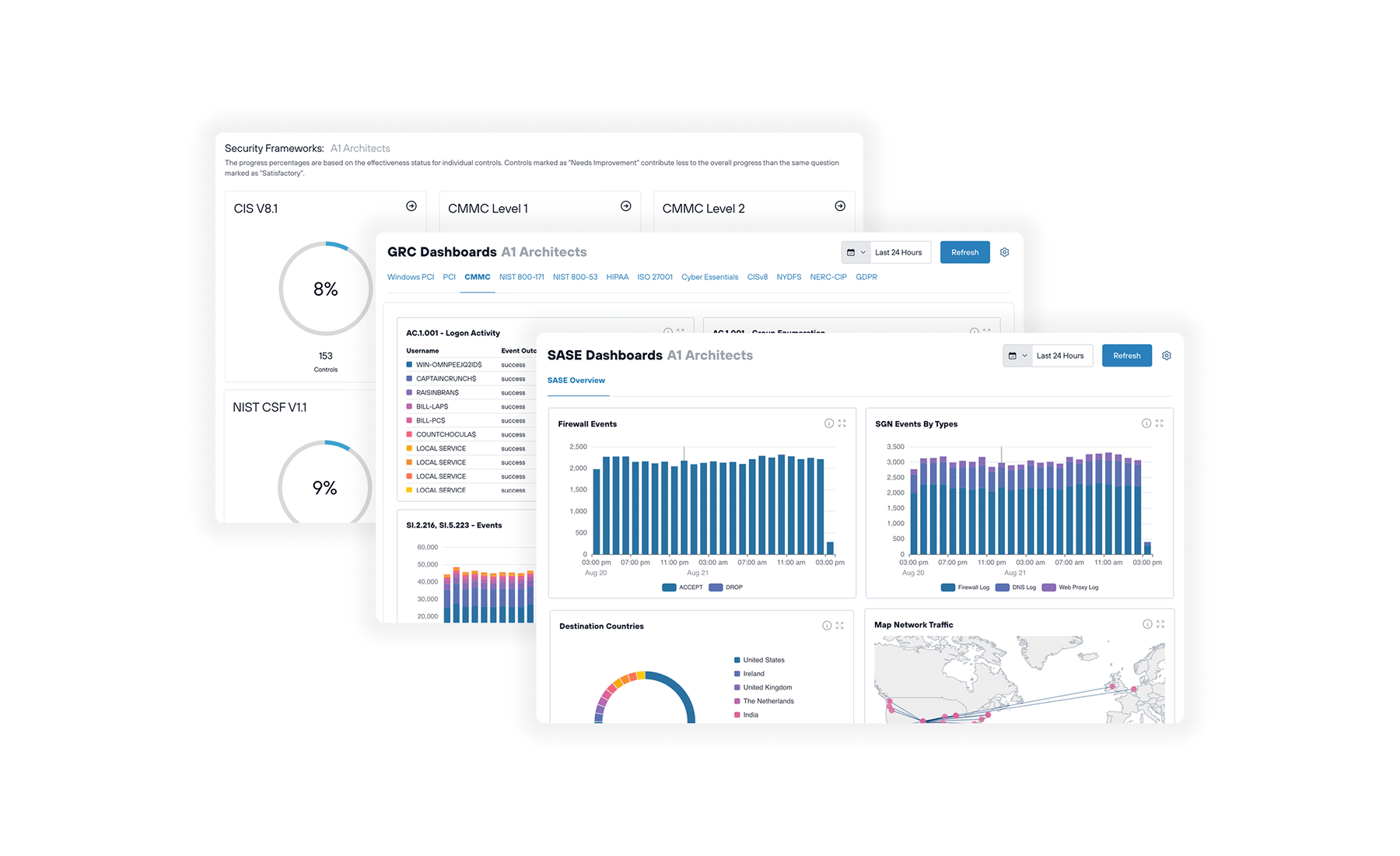
5. Strengthen security posture with risk and compliance management
Growing regulatory requirements (CMMC, NIST CSF, HIPAA, PCI-DSS) demand documented evidence of security controls. Clients need proof, not promises.
Todyl GRC tracks your adherence to regulatory frameworks with pre-built dashboards that map security activities automatically. You're always ready for client questions or audits, with centralized policy repositories and flexible data retention.
Move your clients towards action today
To help you educate your clients, we put together this placemat that covers why they need to move from awareness to action, provides a quick assessment they can take, and then covers actions they can take today to strengthen their defenses.

How Todyl Helps You Take Action
Taking these 5 actions traditionally means managing multiple vendors, juggling integrations, and coordinating across different tools. Todyl consolidates SASE, EDR/NGAV, SIEM, MXDR, and GRC into a single platform. One agent. One interface. One relationship.
This unified approach means you can deploy comprehensive threat, risk, and compliance management without the operational overhead of managing multiple point solutions. Partners reduce their security product count by 50% and reclaim 15 hours per week for client work.
Single platform
Deploy prevention, detection, response, and compliance capabilities through one agent. Partners reduce their security product count by 50%, which means less vendor management and more time for client work.
Consolidate network defense with SASE
Todyl SASE provides fast, reliable, secure access and network threat, risk, and compliance management in a single, fully integrated integrated platform.
Expert partnership
Every package includes MXDR with a named Detection and Response Account Manager. You get transparent collaboration with security experts who know your business.
Identity Threat Detection & Response
Todyl MXDR includes ITDR for Microsoft 365 and Azure environments. When identity attacks happen, our Automated Response can automatically disable compromised before damage is done.
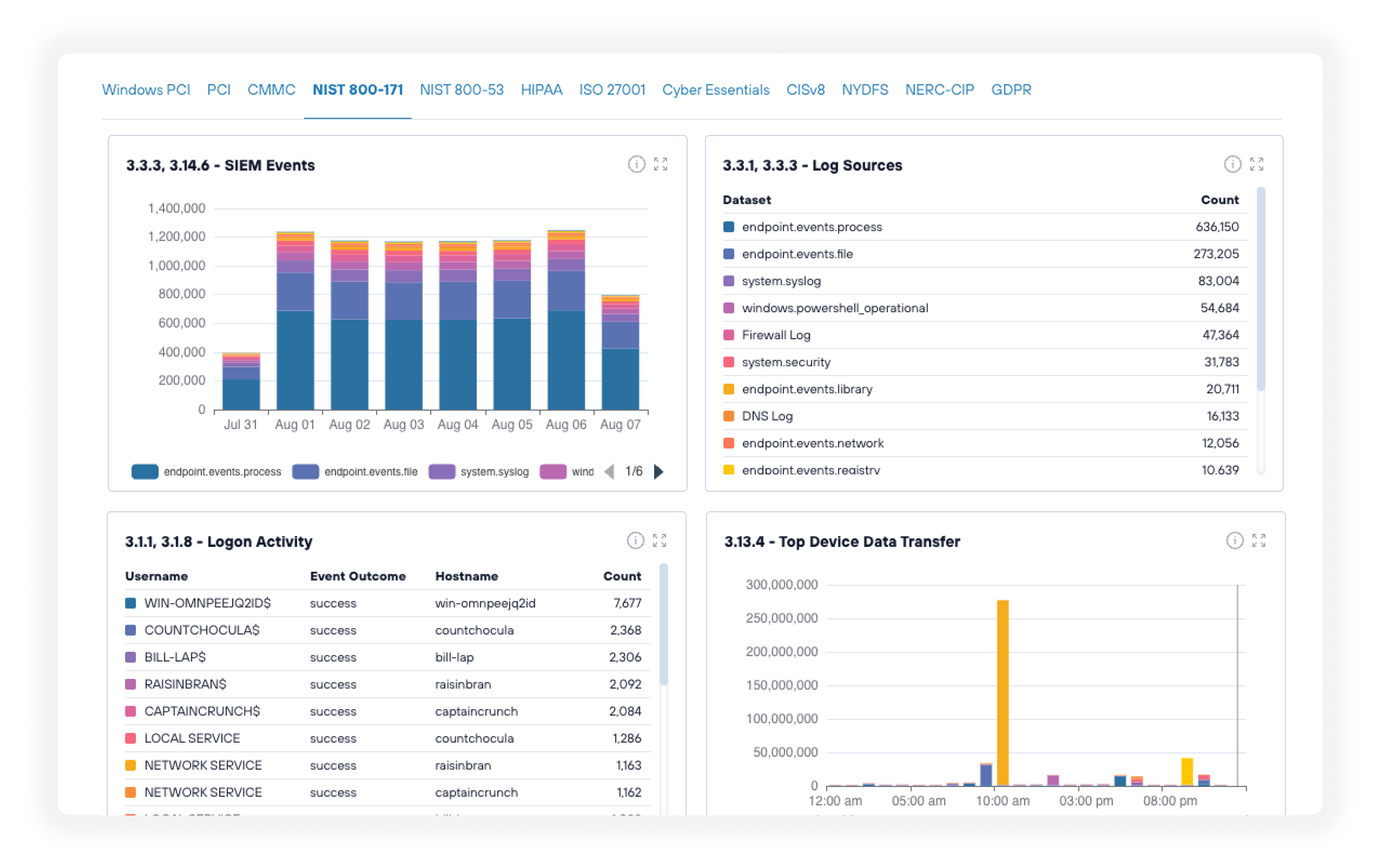
Streamline compliance
Pre-built dashboards for CMMC, NIST CSF, HIPAA, and PCI-DSS with flexible data retention. Serve regulated industries with confidence while helping your clients strengthen their security posture.
Choose the Right Package for Each Client
All packages deliver comprehensive threat, risk, and compliance management through SASE, Endpoint Security, SIEM, MXDR, and GRC with 24/7 expert support and single-agent deployment.
Essentials
Best For
- Businesses building comprehensive security
- Single location operations seeking comprehensive protection
- Basic compliance needs and cyber insurance qualification
What's Included:
- 30-day data retention
- 5 SOAR playbooks
- SASE mobile devices (1:1 ratio)
- Basic compliance frameworks
Advanced
Best For
- Businesses with 1-2 locations
- Enhanced compliance requirements and audit support
- Growing security needs with advanced cyber insurance requirements
Everything in Essentials, plus:
- 90-day data retention
- SSL inspection and 2 Static IPs
- LAN Zero Trust (LZT) segmentation
- SASE mobile devices (1:2 ratio)
- Enhanced compliance frameworks
Complete
Best For
- Highly regulated industries
- Multi-location businesses requiring audit readiness
- Advanced compliance demands and third-party security validation
Everything in Advanced, plus:
- 1-year data retention for forensics
- Unlimited SOAR playbooks
- SASE mobile devices (1:4 ratio)
- Unlimited IPSEC tunnel connections
- Multi-engine download scanning
Testimonials
MSPs Consolidating to Packages Report
50%
Fewer security vendors
52%
Increase in client satisfaction
15 hours
Per week back for other work
